Global Cybersecurity Outlook 2026

3. The trends reshaping cybersecurity
As organizations confront AI threats, geopolitical volatility and supply chain vulnerabilities, the need for resilience has never been clearer.
3.1 AI is reshaping risk, accelerating both offence and defence
Developments in AI are reshaping multiple domains, including cybersecurity. Implemented well, these technologies can assist and support human operators in detecting, defending and responding to cyberthreats. However, they can also pose serious risks such as data leaks, cyberattacks and online harms if they malfunction, or are misused. Governments must take a forward-looking, practical and collaborative approach to developing and using emerging technologies safely, as their capabilities and risks continue to evolve. The risks transcend borders, and the challenge is to maximize AI’s benefits, including to strengthen our cyber resilience, while minimizing its risks.
— Josephine Teo, Minister for Digital Development and Information and Minister-in-Charge of Cybersecurity and Smart Nation Group, Singapore
AI is anticipated to be the most significant driver of change in cybersecurity in the year ahead, according to 94% of survey respondents. AI is reshaping the cybersecurity landscape across three interconnected dimensions. First, the widespread integration of AI systems introduces an expanded attack surface, creating novel vulnerabilities that traditional controls were not designed to address. Second, defenders are harnessing AI to strengthen their cyber capabilities – augmenting detection, accelerating incident response and automating high-volume analytical tasks. Third, threat actors are leveraging AI to enhance the scale, speed, sophistication and precision of their attacks, driving a new generation of automated exploitation and targeted social engineering (see Section 3.3).
Together, these dynamics illustrate the dual-use nature of AI, both as a force multiplier for defence and as a catalyst for attackers. As this technological competition intensifies, organizations are shifting from reactive to proactive security, while reassessing governance, validation and oversight at every stage of AI adoption.
Figure 7: Impacts of AI on cybersecurity
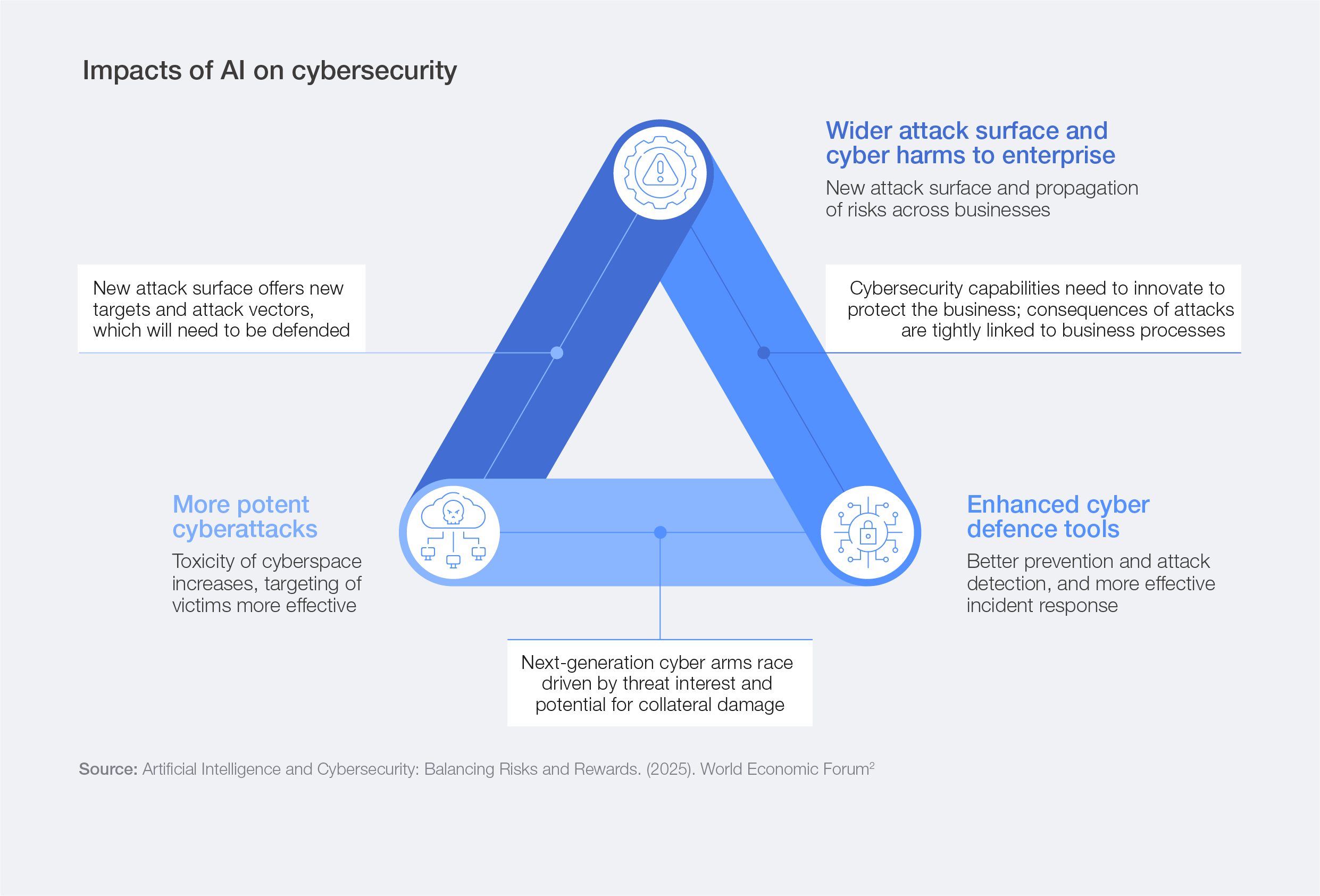
AI’s benefits are contingent on disciplined execution. Poorly implemented solutions can introduce new risks – misconfiguration, biased decision‑making, over‑reliance on automation and susceptibility to adversarial manipulation – unless organizations embed robust guardrails, security‑by‑design practices and continuous monitoring. The implication is clear: AI can improve cybersecurity, but only when deployed within sound governance frameworks that keep human judgement at the centre. At the same time, too many controls can create friction, so it is essential to strike a careful balance.
Security of AI: from awareness to action
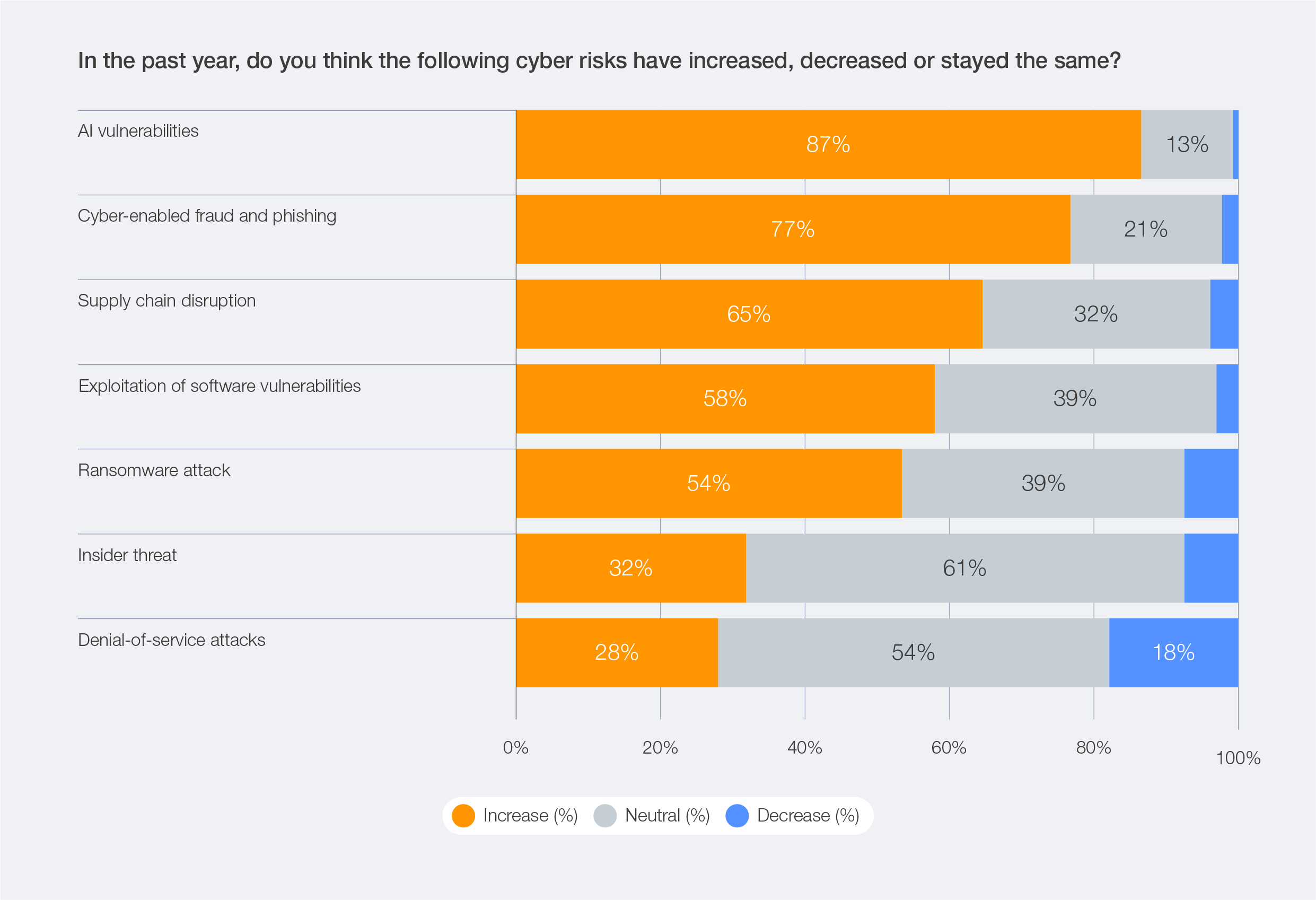
According to the Global Cybersecurity Outlook 2026 survey, 87% of respondents identified AI-related vulnerabilities as the fastest-growing cyber risk over the course of 2025.
Figure 8: Perception of increase or decrease in cyber risks over the past year
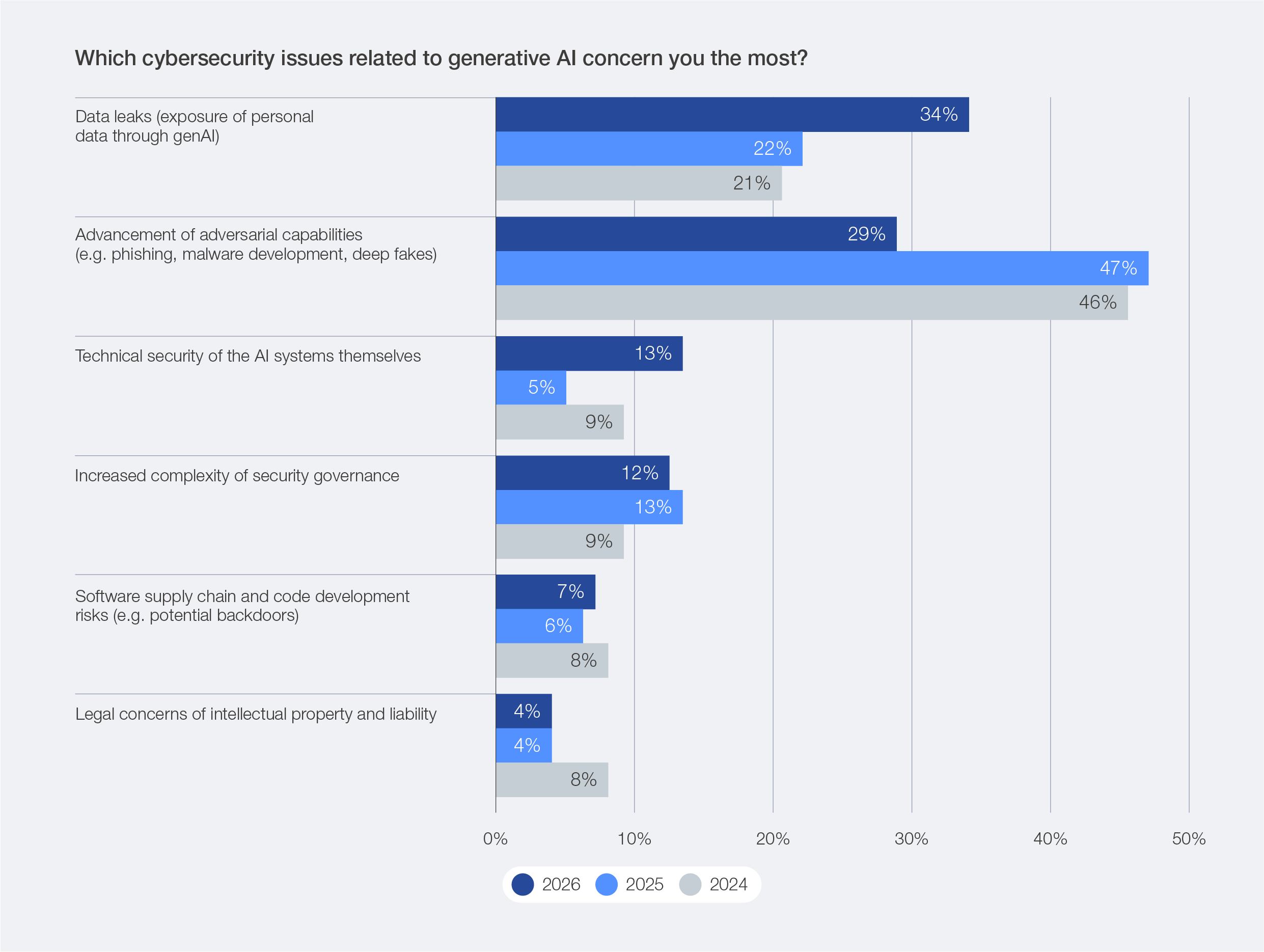
Data leaks associated with genAI (34%) and the advancement of adversarial capabilities (29%) stand out as leading concerns for 2026. This marks a striking reversal from previous years – in 2025, advancement of adversarial capabilities topped the list at 47% compared to only 22% for data leaks associated with genAI. The shift underscores a turning point in the AI risk landscape for the upcoming year: while the “AI arms race” between attackers and defenders continues to intensify, attention is pivoting from purely offensive innovation with AI towards the unintended exposure and misuse of sensitive data through generative and agentic systems.
Figure 9: Top concerns related to genAI
Growing awareness of AI-related cybersecurity risks is reflected in the increasing focus on the secure use of AI. The Global Cybersecurity Outlook 2025 highlighted a significant gap between the widespread recognition of AI-driven risks and the rapid adoption of AI technologies without adequate safeguards. By 2026, however, this picture is changing: the share of organizations assessing the security of their AI tools has nearly doubled – from 37% in 2025 to 64% in 2026 – indicating that more organizations are introducing structured processes and governance models to manage AI securely and responsibly.
Figure 10: Percentage of organizations with processes in place to assess AI security
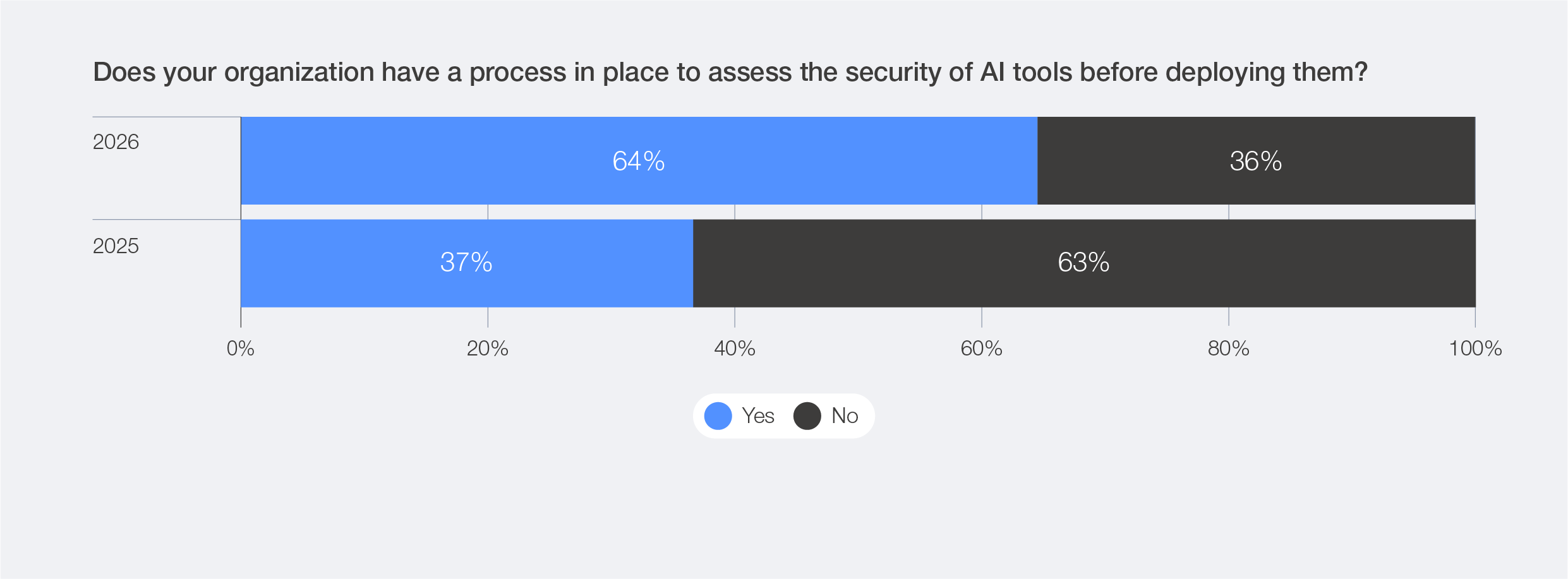
Figure 11: Frequency of AI security assessments in organizations
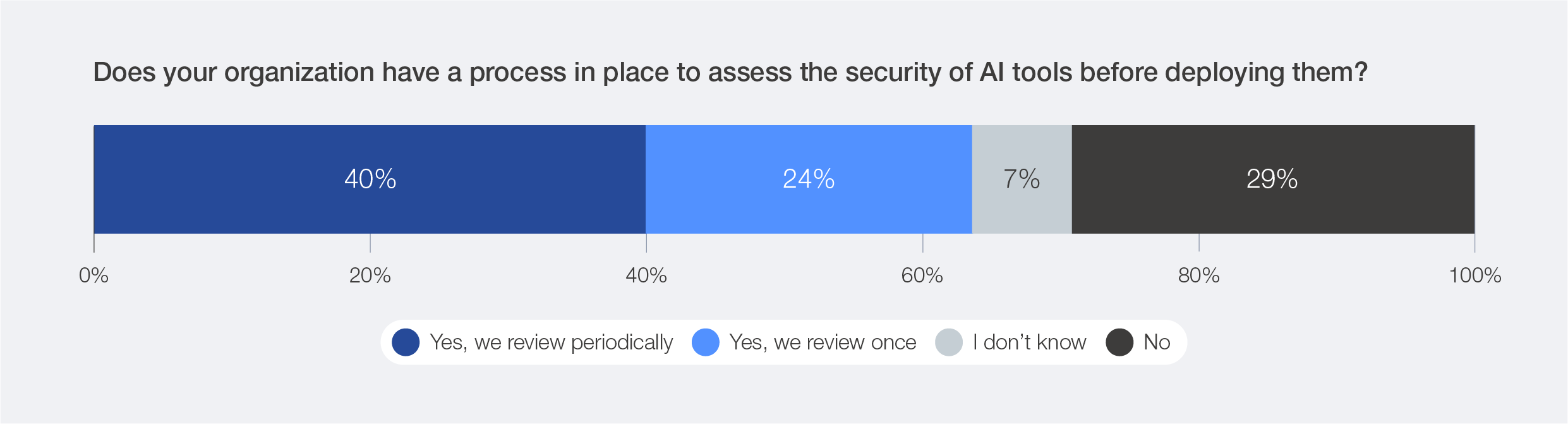
In the 2026 survey, 40% of organizations reported conducting periodic reviews of their AI tools before deploying them, rather than only doing a one-time assessment (24%) – a clear sign of progress towards continuous assurance. However, roughly one-third still lack any process to validate AI security before deployment, leaving systemic exposures even as the race to adopt AI in cyber defences accelerates.
The market’s drive to adopt new AI features often outpaces security readiness, creating exploitable vulnerabilities.3 In response to these emerging risks, a number of fundamental measures should be prioritized to secure AI at the infrastructure level. This includes protecting the data used in the training and customization of AI models from breaches and unauthorized access. AI systems should be developed with security as a core principle, incorporating regular updates and patches to address potential vulnerabilities. It is also critical for organizations to deploy robust authentication and encryption protocols to ensure the protection of customer interactions and data.4
Box 1: The widespread adoption of AI agents
As AI agents become more widely adopted, they are poised to transform how digital systems are designed and developed. AI agents can enhance efficiency, responsiveness and scalability by automating complex or repetitive activities with speed and consistency, but their integration can challenge traditional security frameworks, redefining roles and processes, while raising fundamental questions about decision-making and the prioritization of alerts.
The multiplication of identities and connections makes managing their credentials, permissions and interactions just as critical – and likely even more complex – as managing those of human users. As outlined in the World Economic Forum’s report AI Agents in Action: Foundations for Evaluation and Governance, without strong governance, agents can accumulate excessive privileges, be manipulated through design flaws or prompt injections, or inadvertently propagate errors and vulnerabilities at scale. Their speed and persistence amplify these risks, underscoring the need for continuous verification, audit trails and robust accountability structures grounded in zero-trust principles that treat every interaction as untrusted by default.5
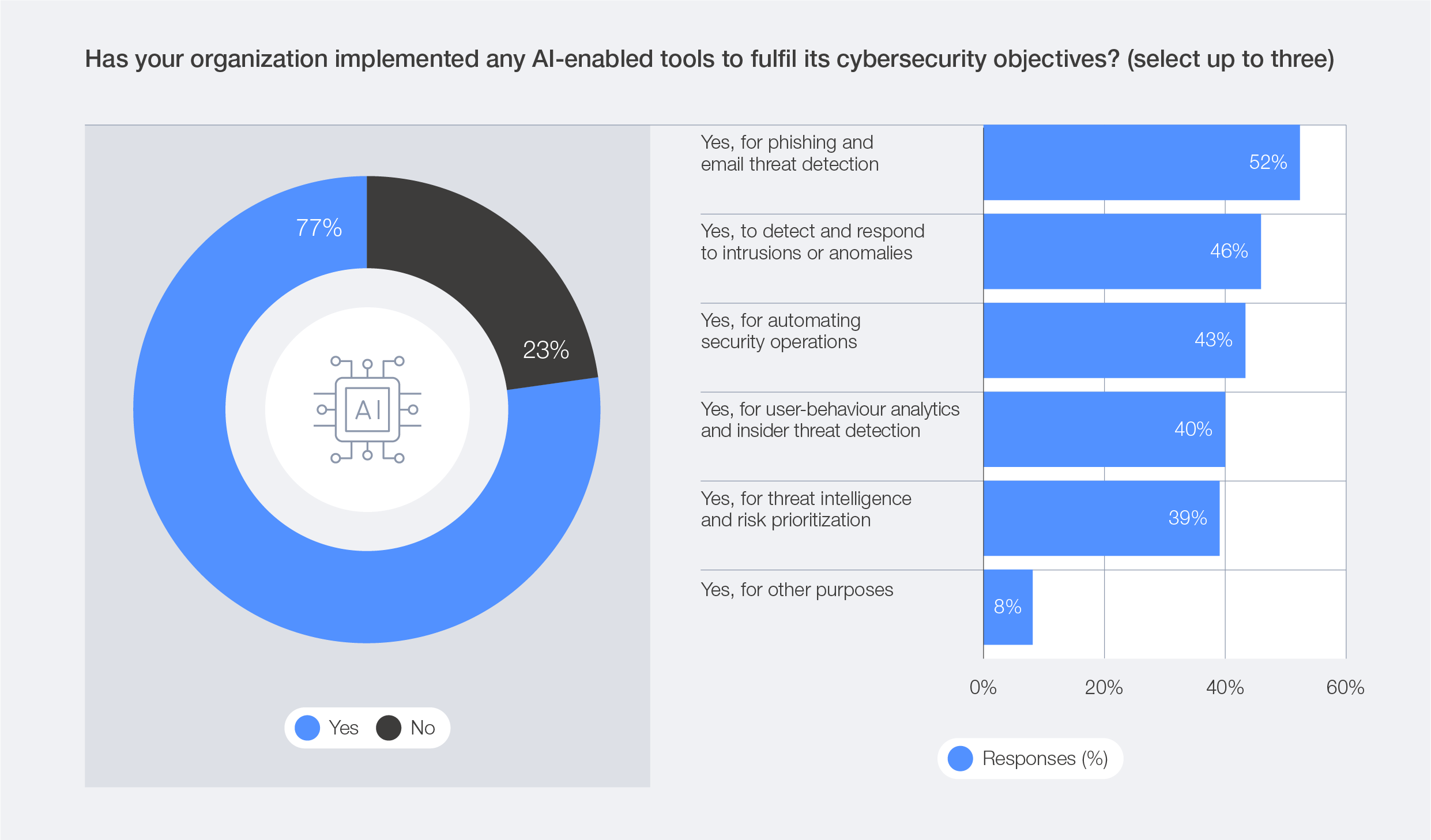
AI for cybersecurity
AI is fundamentally transforming security operations – accelerating detection, triage and response while automating labour-intensive tasks such as log analysis and compliance reporting. AI’s ability to process vast datasets and identify patterns at speed positions it as a competitive advantage for organizations seeking to stay ahead of increasingly sophisticated cyberthreats. The survey data reveals that 77% of organizations have adopted AI for cybersecurity, primarily to enhance phishing detection (52%), intrusion and anomaly response (46%) and user-behaviour analytics (40%).
Figure 12: How organizations are implementing AI for cybersecurity
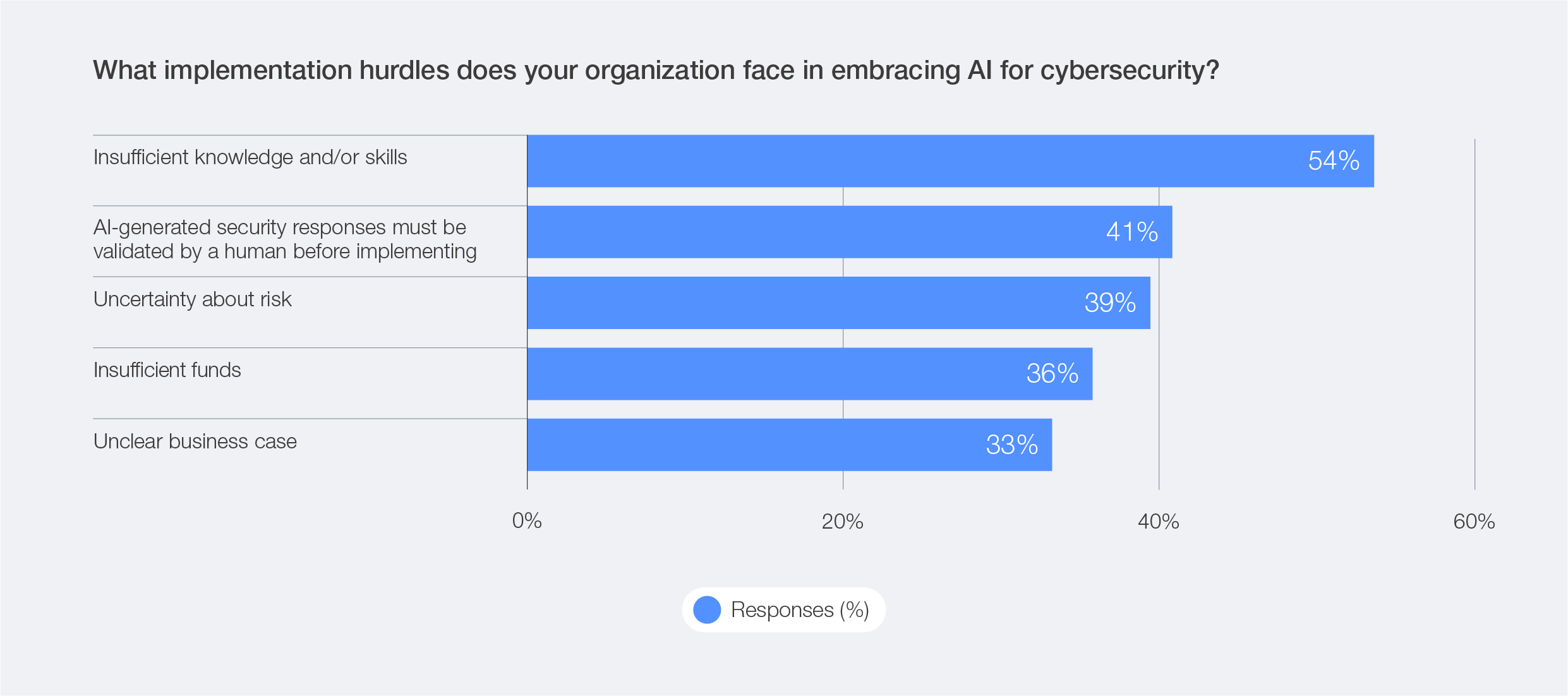
Addressing the practical challenges of AI adoption in cybersecurity, organizations consistently identify insufficient knowledge and/ or skills (54%) to deploy AI for cybersecurity, the need for human oversight (41%) and uncertainty about risk (39%) as the main hurdles. These findings indicate that trust is still a barrier to widespread AI adoption.
Criminals are always willing to use all possible ways to get access to value, much of which is contained in the cyber infrastructure. Consequently, to stay ahead, those of us who defend must use every tool at our disposal – which now includes agentic AI.
— Arvind Krishna, Chief Executive Officer, IBM
Figure 13: Barriers in AI implementation for cybersecurity
As organizations navigate the integration of AI into their security operations, the balance between automation and human judgement becomes increasingly critical. While AI excels at automating repetitive, high-volume tasks, its current limitations in contextual judgement and strategic decision-making remain clear. Over-reliance on ungoverned automation risks creating blind spots that adversaries may exploit.
This evolving dynamic is reshaping the role of cybersecurity professionals, highlighting the importance of adapting skill sets to meet new demands. According to the World Economic Forum’s The Future of Jobs Report 2025, “networks and cybersecurity” are among the top three fastest-growing skills projected for 2030 – alongside AI and big data and technological literacy – reinforcing the urgency for targeted upskilling and continuous learning.6
Rather than replacing human expertise, AI is enabling specialists to shift their focus towards strategic oversight, governance and policy while delegating routine operational tasks to automation. This transition demands new skill sets, blending technical proficiency with strategic and ethical considerations, and underscores the growing importance of AI literacy across security teams.
The priorities for organizations are clear: invest in AI literacy and secure-use skills, and embed governance and validation, without creating new single points of failure. A collaborative model, anchored in security-by-design principles, emerges as the recommended path forward – enabling organizations to harness AI’s advantages while mitigating vulnerabilities and ensuring innovation strengthens, rather than compromises, cybersecurity.
How industries are adopting AI for cybersecurity
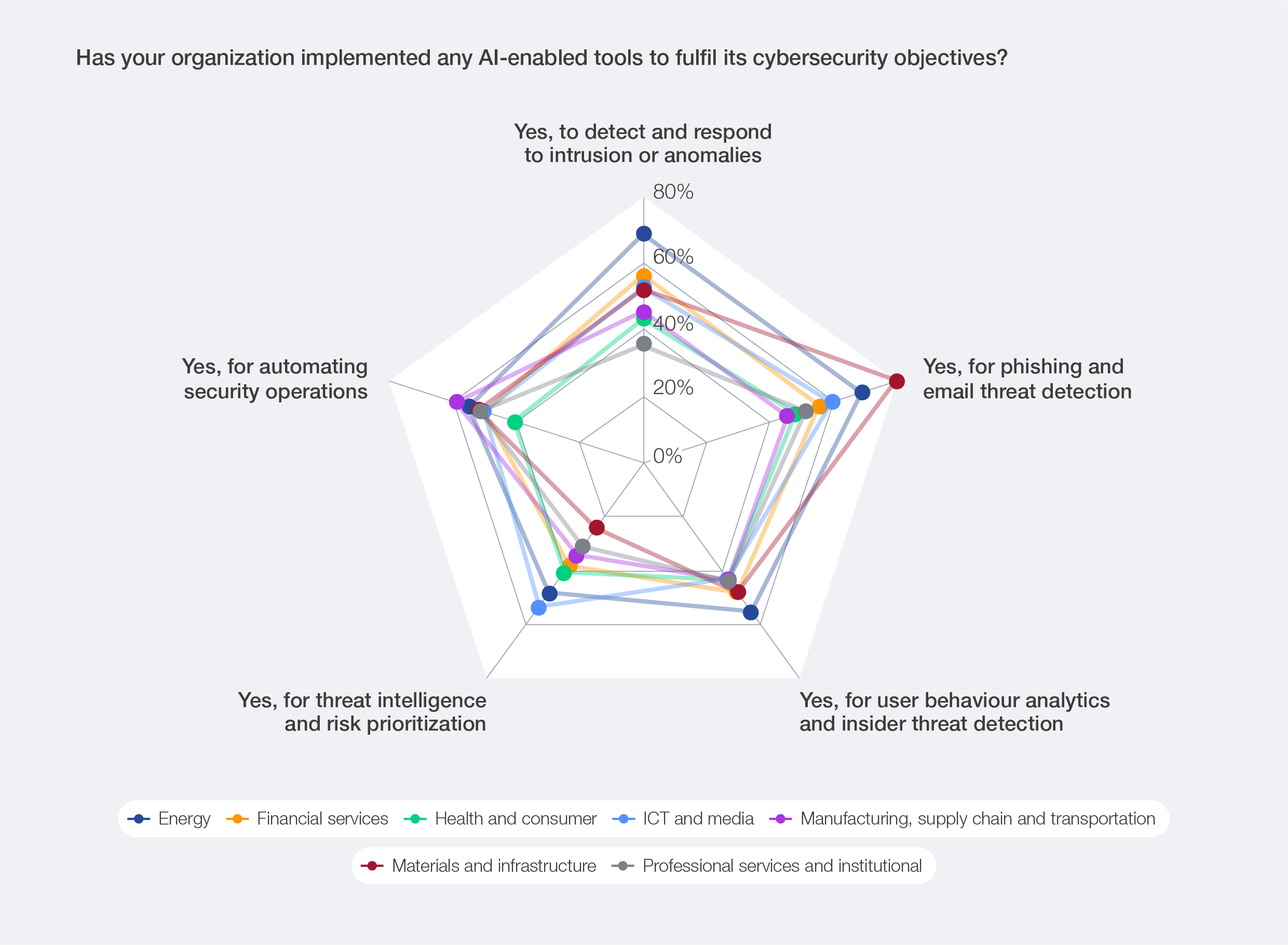
The adoption of AI tools to augment cybersecurity capabilities varies across industries, reflecting sectorspecific risk profiles and operational needs. The energy sector emphasizes intrusion and anomaly detection (according to 69% of respondents who have implemented AI for cybersecurity); the materials and infrastructure sector prioritizes phishing protection (80%); and the manufacturing, supply chain and transportation sector reports greater use of automated security operations (59%). These differences not only reflect sectoral risk profiles and operating constraints but also collectively point to a maturing portfolio of AI-enabled cyber defence capabilities that spans detection, intelligence, analytics and orchestrated cyber defence.
The differences in AI adoption for cybersecurity will be analysed in Section 3.6.
Figure 14: Use cases of AI for cyber defence across industries
3.2 Geopolitics is a defining feature of cybersecurity
In an increasingly fragmented global environment – marked by conflicts, geoeconomic tensions, trade wars, sanctions and growing technological competition – geopolitics has become a defining force shaping cybersecurity.
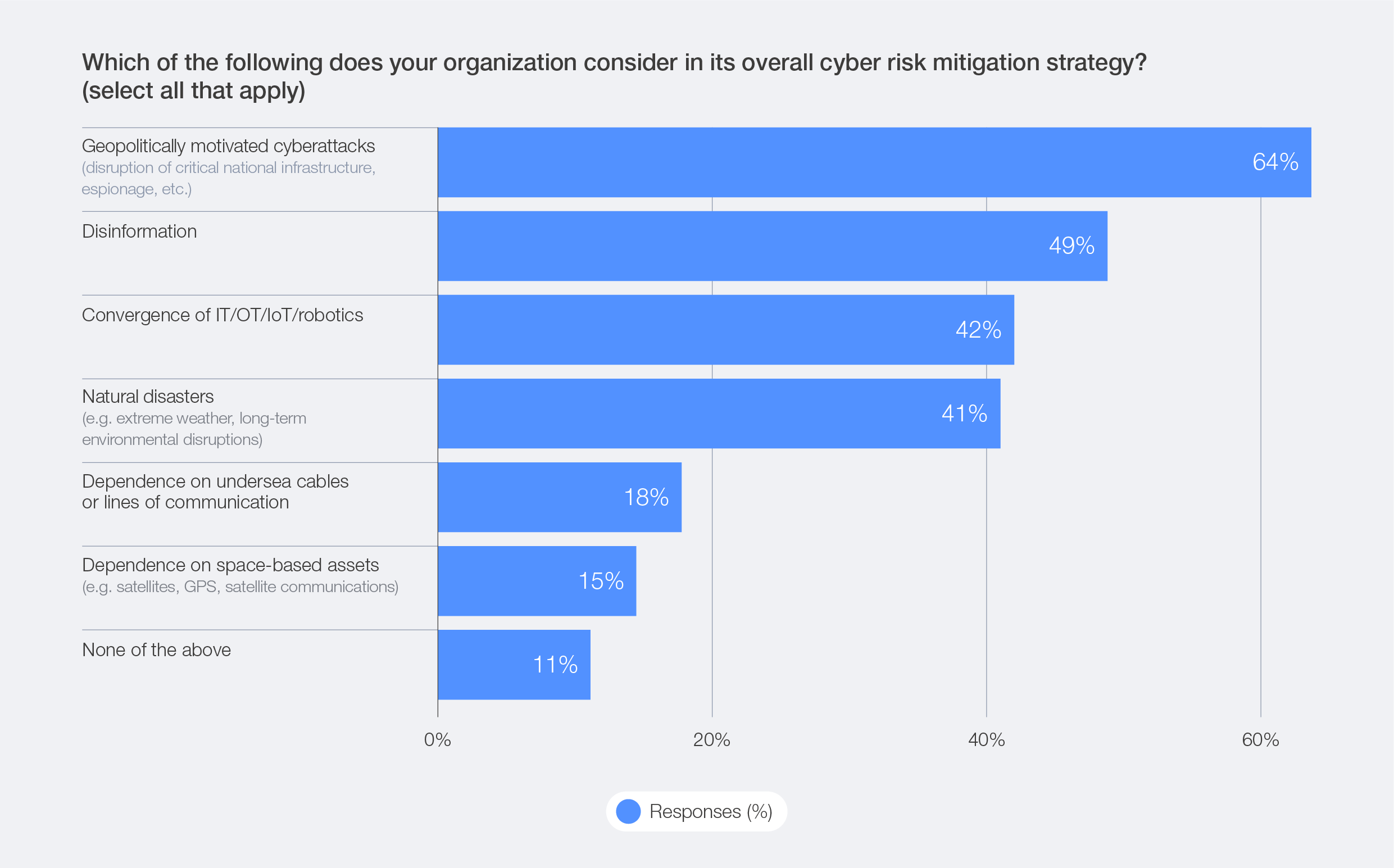
The Global Cybersecurity Outlook 2026 survey data reveals that, although the percentage of organizations changing their cybersecurity strategy due to geopolitics has declined from 93% in 2023 to 66% in 2026, geopolitics remains the top factor influencing overall cyber risk mitigation strategies. This suggests that the initial wave of adaptations following the geopolitical turmoil that dominated the headlines in 2022 and 2023 has passed, and that geopolitical risk is now a major factor shaping cyber defence.
Figure 15: Year-over-year evolution of cybersecurity strategy shifts due to geopolitical volatility
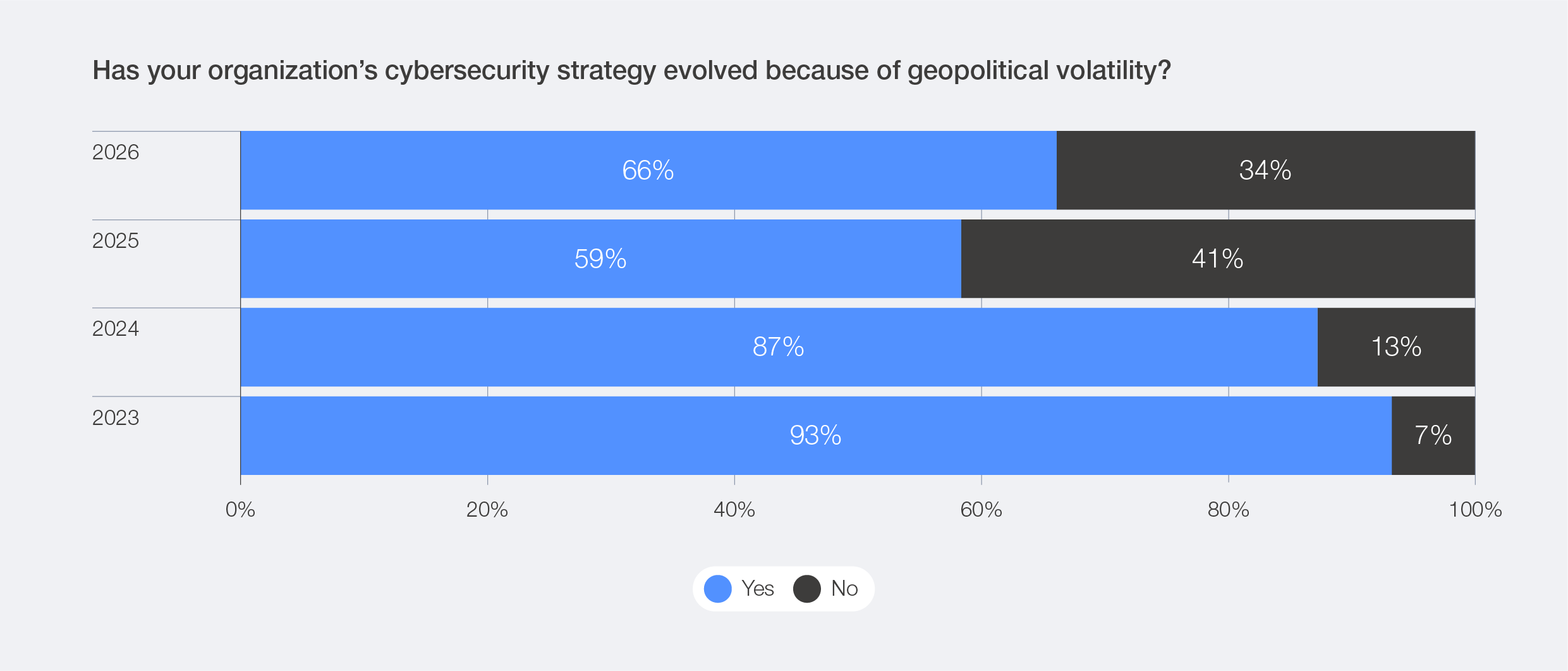
Figure 16: Top considerations for cyber risk mitigation strategies
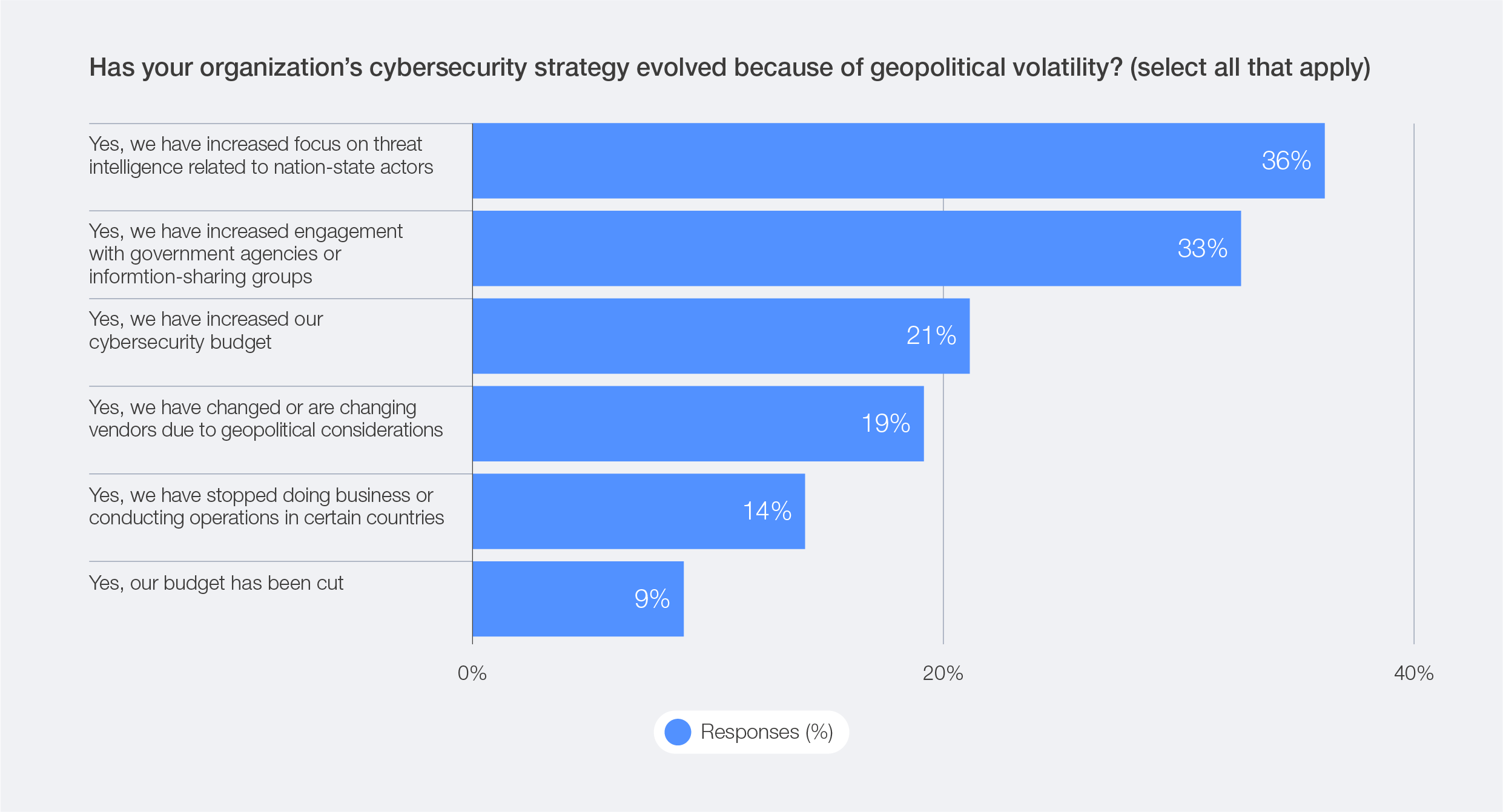
Organizations are increasingly shifting from isolated defence to intelligence-driven collaboration. In response to geopolitical volatility, survey respondents identified a stronger focus on threat intelligence and deeper engagement with government agencies as the top two drivers of change in their cybersecurity strategies. This trend indicates a growing recognition that navigating an uncertain geopolitical landscape demands collaboration and shared situational awareness.
Figure 17: Aspects of shifting cybersecurity strategy due to geopolitical volatility
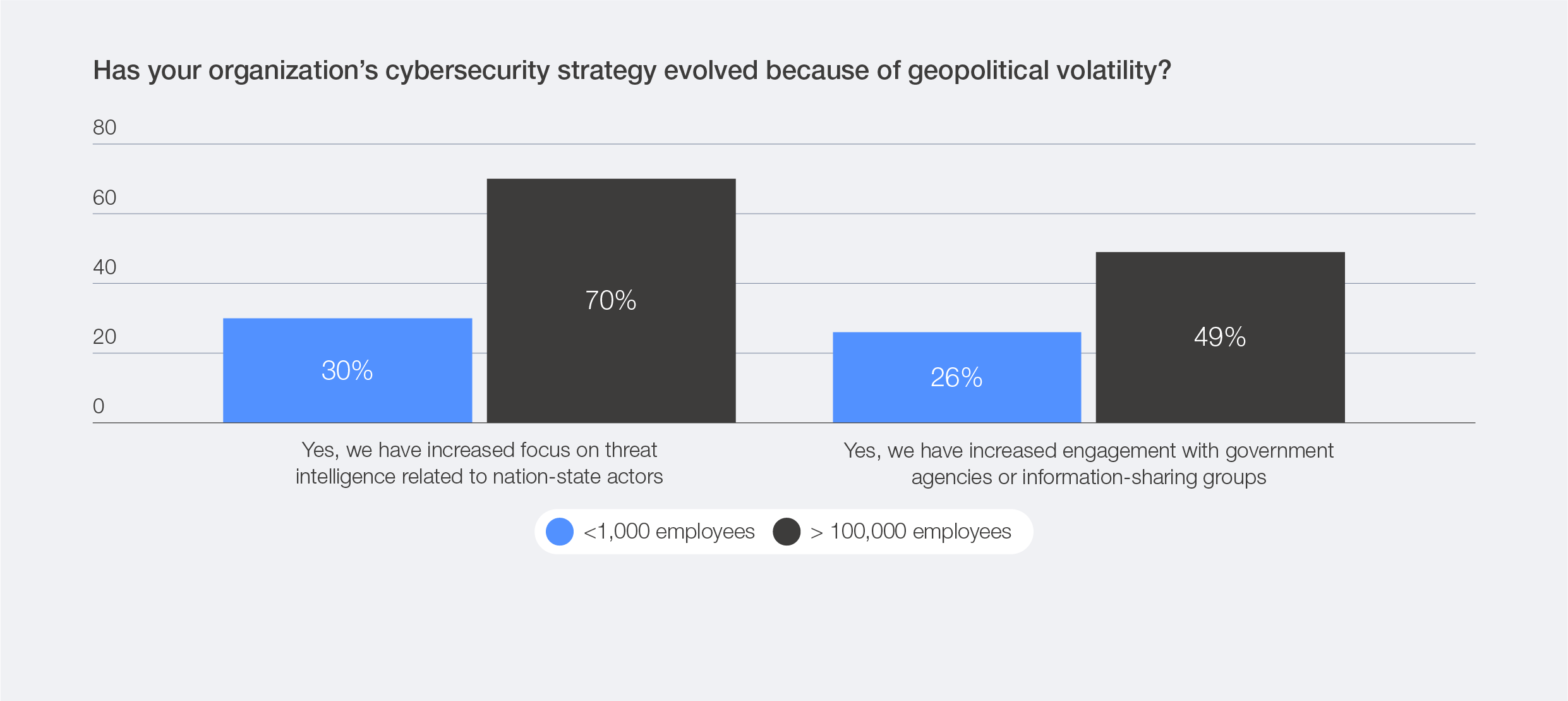
The shift towards intelligence-driven collaboration is being led primarily by global organizations with a larger number of employees, which are inherently more exposed to geopolitical volatility due to their global operations. These large employers are proactively seeking greater collaboration to manage this heightened exposure – leveraging their scale and resources to strengthen resilience.
Data shows that 70% of the largest employers (those with more than 100,000 employees) have increased their focus on threat intelligence, compared to only 30% of small employers (those with 1,000 employees or fewer).7 Similarly, 49% of these large employers have deepened their engagement with government agencies or information-sharing groups, versus 26% of small employers. In contrast, those smaller organizations, with limited staff and narrower geographic footprints, appear to be less aware of direct geopolitical pressures and often have less capacity to participate in collective security efforts. This may mean relying more frequently on risk acceptance rather than active mitigation in response to geopolitical volatility.
Figure 18: Strategy shifts due to geopolitical volatility among small and very large employers (by headcount)
Local events – global impact
Geopolitical instability and armed conflicts are reshaping the cyberthreat landscape, creating complex and unpredictable conditions for organizations. As global fragmentation deepens – driven by conflicts, sanctions and technological rivalry – cybersecurity is emerging as a critical extension of geopolitical competition.
The large-scale power outage experienced in the Iberian Peninsula, while not in itself the result of a cyberattack, highlighted the impact a cyberattack could have on such critical national infrastructure. Ongoing instability in the wake of the war in Ukraine has coincided with a rise in hybrid attacks, using drones to target European airports and other critical infrastructure, along with the spread of disinformation, which have further destabilized the regional security landscape.8 Beyond Europe, escalating geopolitical rivalries and conflicts across the Indo-Pacific, Middle East and Africa require organizations to maintain heightened vigilance as risks intensify across regions and industries. Of particular concern to participants in focus groups for this report was the use of advanced offensive cyber capabilities by nation-state actors to hack telecommunications networks in the United States.9,10,11
The shift to a paradigm of more global confrontation – for example, by using trade policies, including tariffs and export restrictions – is reshaping alliances and technology dependencies. Political tensions are contributing to a growing fragmentation of global technology ecosystems, as countries diversify their partnerships and supply chains. Political and economic tensions are also driving countries and corporations to reconfigure supply chains, reshore manufacturing and cultivate “trusted” regional partners. The rush to establish alternative suppliers, logistics channels or data-hosting arrangements often outpaces cyber due diligence, expanding the attack surface across less-secure networks and third parties. As tariffs and policy shifts ripple through industries, cybersecurity risk management must evolve in tandem – treating trade disruptions as triggers for renewed threat modelling and vendor-risk reassessment.12
In this volatile environment, cyber operations have become tools of diplomacy and influence – used to shape political outcomes and disrupt trade – further reinforcing the link between geopolitical uncertainty and organizational cyber risk exposure. Although geopolitical volatility continues to weigh on strategic decisionmaking, a concerning trend has emerged: reductions in cybersecurity budgets that may constrain organizational capacity to manage growing threats. Survey data shows that 12% of organizations based in North America and 13% of organizations based in Latin America and the Caribbean have reported cutting cybersecurity budgets due to geopolitical volatility.
As state-sponsored attacks and espionage campaigns intensify, organizations face mounting challenges in forecasting cyber risks and aligning strategies with shifting global conditions. Participants in focus group interviews for this report warn that these pressures will persist, reinforcing the need for adaptive, resilient cyber strategies despite constrained budgets.
Geopolitical tensions driving critical infrastructure vulnerabilities
Geopolitical tensions particularly expose threats and vulnerabilities in the critical national infrastructure that supports society and underpins the operations of countless organizations. Sectors such as energy, water and transportation are increasingly targeted in cyber warfare campaigns, where the interconnected nature of systems amplifies the impact of disruptions. A striking illustration came in April 2025 when a Norwegian hydropower dam was hacked, opening a floodgate and releasing 500 litres of water per second for four hours, in what officials described as a deliberate act of sabotage.13
Alarmingly, 31% of the Global Cybersecurity Outlook survey participants express lack of confidence in their nation’s ability to respond effectively to major cyber incidents, which is up from 26% last year. This indicates a growing sense of uncertainty and heightened exposure.
Figure 19: Overall confidence in national cyber response to critical infrastructure attacks
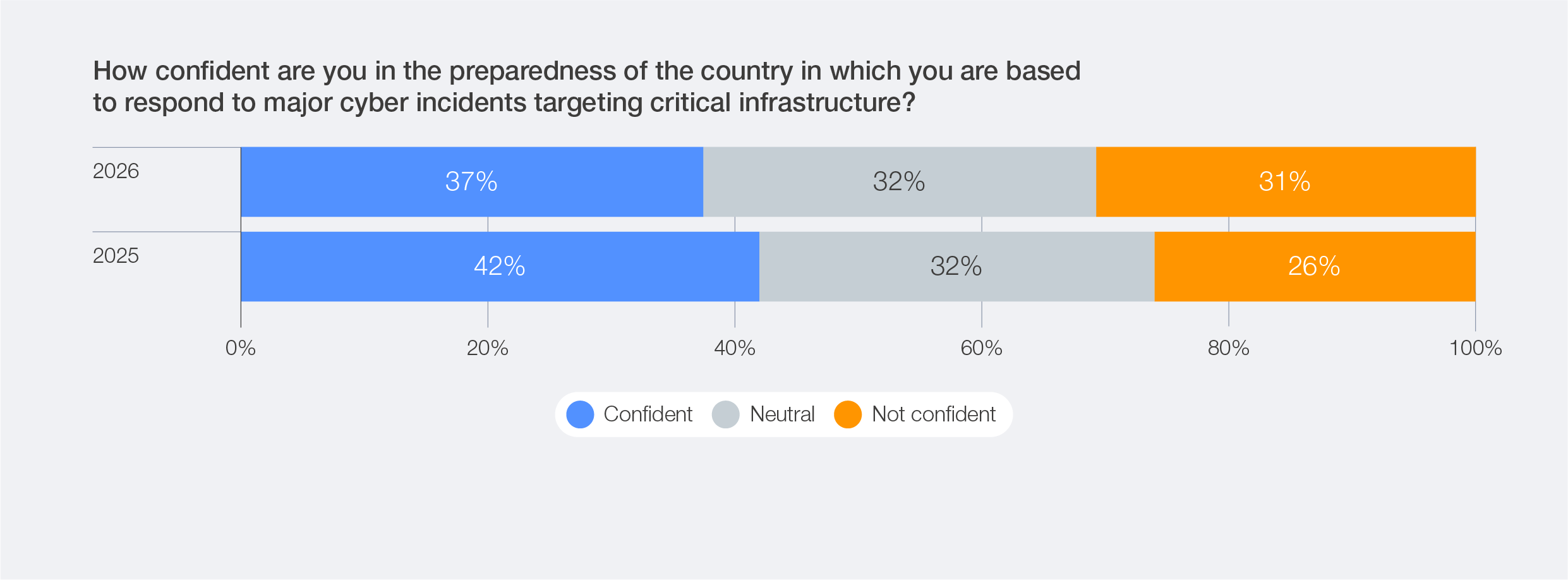
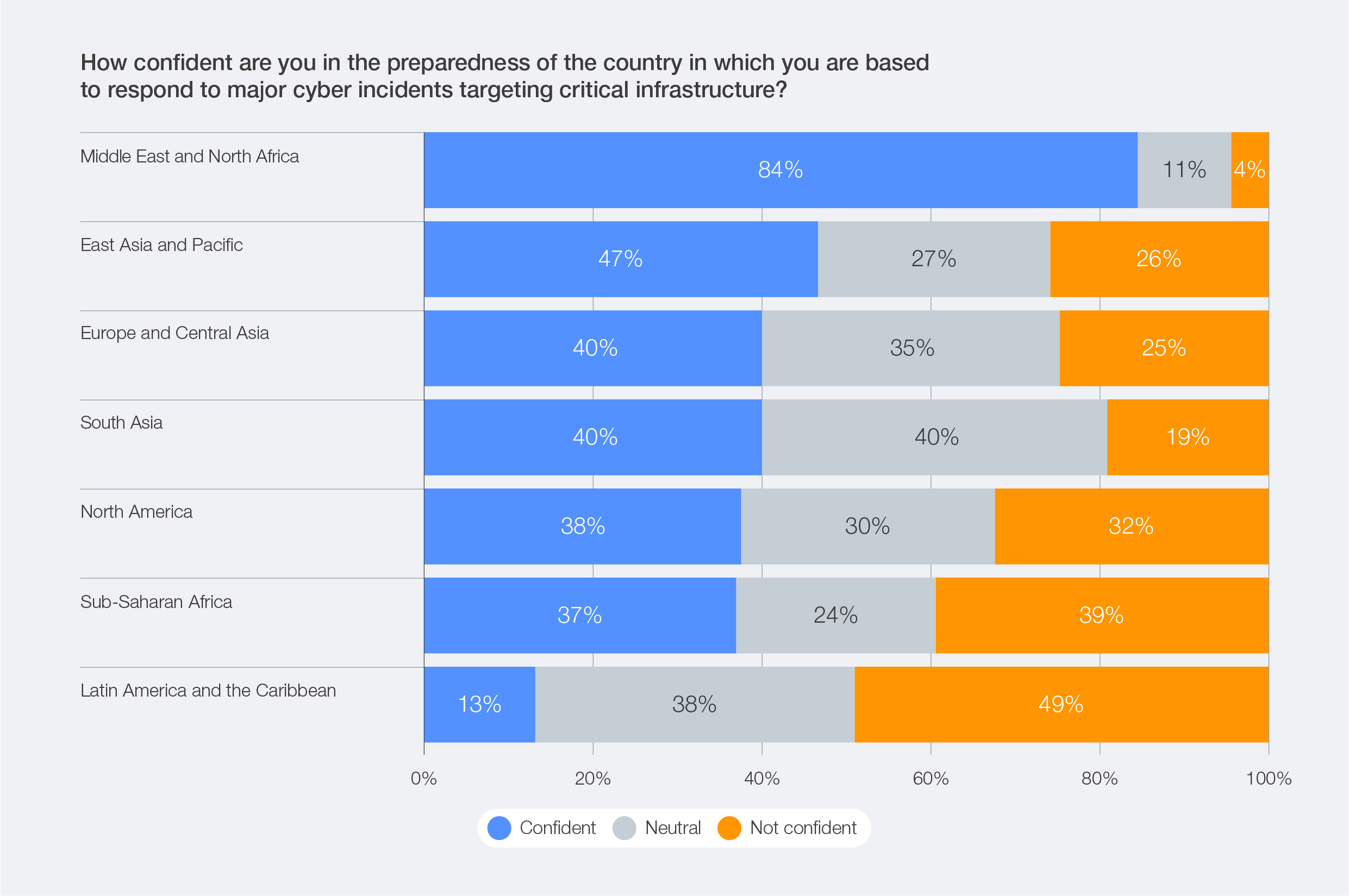
Respondents’ perceptions of their country’s ability to protect critical national infrastructure vary significantly across regions. While a high degree of confidence is expressed by respondents from the Middle East and North Africa (84% of respondents), far less confidence is expressed by respondents based in Latin America and the Caribbean (13%).
Figure 20: Regional overview: Confidence in national cyber response to critical infrastructure attacks
Box 2: Strengthening cyber readiness through coordinated national action
Saudi Arabia’s cybersecurity resilience is built on a clear national principle: strength begins with people. When individuals, organizations and sectors are equipped with the right awareness and skills, they form a unified shield that reinforces the nation’s digital security and resilience.
Rooted in this principle, the National Cybersecurity Authority (NCA) has established a whole-of-nation model that elevates readiness at every level of society. The NCA sets strategic direction and is supported by the Saudi Information Technology Company (SITE), which translates these priorities into actionable, high-impact programmes.
Through its cyber drills, SITE delivers high-fidelity simulations that enhance preparedness for evolving cybersecurity threats. During major events such as Hajj, these exercises stress-test containment, crisis management and cross-sector coordination, ensuring that readiness is both operational and proven.
In parallel, nationwide awareness initiatives distil technical insights into accessible, culturally attuned guidance that strengthens daily vigilance. These campaigns extend from national programmes to individual engagement, aligning stakeholders across sectors to address risks such as phishing and AI-driven misinformation.
Together, NCA and SITE are shaping a cybersecurity culture where awareness, preparedness and coordinated action are embedded across the entire nation.
Cybersecurity in the sovereignty era
The uneven confidence across regions points to a broader shift in how nations perceive cyber resilience – from a technical challenge to a question of sovereignty and self-reliance. As nations seek to protect critical infrastructure, many are re-evaluating their dependencies on foreign technology providers and global supply chains. This connection between infrastructure protection and digital autonomy has become a defining feature of modern cybersecurity policy.
Over the course of 2025, economic uncertainty and geopolitical instability have become deeply intertwined, amplifying global cyber risk and complicating organizations’ ability to anticipate and mitigate emerging threats. As political tensions and trade disputes reshape alliances and technology dependencies, the world is witnessing growing fragmentation across digital and technological ecosystems. This renewed focus on digital sovereignty reflects an urgent drive by states and organizations to safeguard autonomy, control critical assets and reduce exposure to external shocks.
The term “cyber sovereignty” is often used to mean the application of traditional state sovereignty rights and obligations (i.e. control of territory, non-intervention, jurisdiction) to the domain of cyberspace.14 The concept is complicated by the fact that cyberspace doesn’t map neatly onto physical territory (servers, cables, data flows cross jurisdictions), so applying conventional sovereignty (which is territory-based) becomes challenging.
At the organizational level, concerns over sovereignty have become increasingly tangible. Governments, public institutions and private enterprises alike are reassessing dependencies on foreign technology providers and global cloud infrastructure, in light of geopolitical tensions and supply chain vulnerabilities. For instance, several European actors – including municipalities such as Copenhagen, in Denmark, and federal agencies in Germany – have begun shifting towards sovereign or regionally managed cloud solutions to ensure compliance with national data-protection mandates and to mitigate perceived risks associated with extraterritorial control of data.15 Similar debates are unfolding elsewhere as organizations weigh the benefits of global interoperability against the imperative of maintaining control over critical digital assets and sensitive information.
This trend illuminates a broader recalibration of trust – not only in systems and technologies, but in the geopolitical reliability of the ecosystems that underpin them. The growing attention to sovereignty emphasizes the tension between preserving openness and interoperability and safeguarding national autonomy, control and resilience against external disruptions.
As the threat landscape evolves and AI increasingly powers offensive operations in cyberspace, we must step up our work on the resilience of our critical infrastructure and connectivity. The EU stands ready to work with like-minded partners to protect what is today the digital backbone of our economy and society. Looking ahead, our priority is to boost investments in cyber to strengthen Europe’s industrial capabilities and harness deep tech for better detection and anticipation, invest in people to close the cyber skills gap, and deepen intelligence sharing so that we can spot and address vulnerabilities faster.
— Henna Virkkunen, Executive Vice-President for Tech Sovereignty, Security and Democracy, European Commission
3.3 The evolving landscape of cybercrime: AI, fraud and the global response
Over the course of 2025, several high-profile cybercrime cases have dominated the headlines, with cyberattacks disrupting retail, businesses and manufacturing operations – and even targeting nurseries.16
Ransomware continues to be the leading concern for CISOs; by contrast, CEOs tend to be more concerned on the broader business impacts of frauds. For CISOs this concern reflects the significant operational disruption a successful ransomware attack can inflict on the availability of critical information technology (IT) and operational technology (OT) systems. Many of the major cyber incidents that made the headlines in 2025 were, in fact, driven by ransomware demands. As one of the most lucrative tactics for cybercriminals, ransomware remains a persistent threat, and the increasing integration of AI into attack methods is expected to make these attacks even more effective.
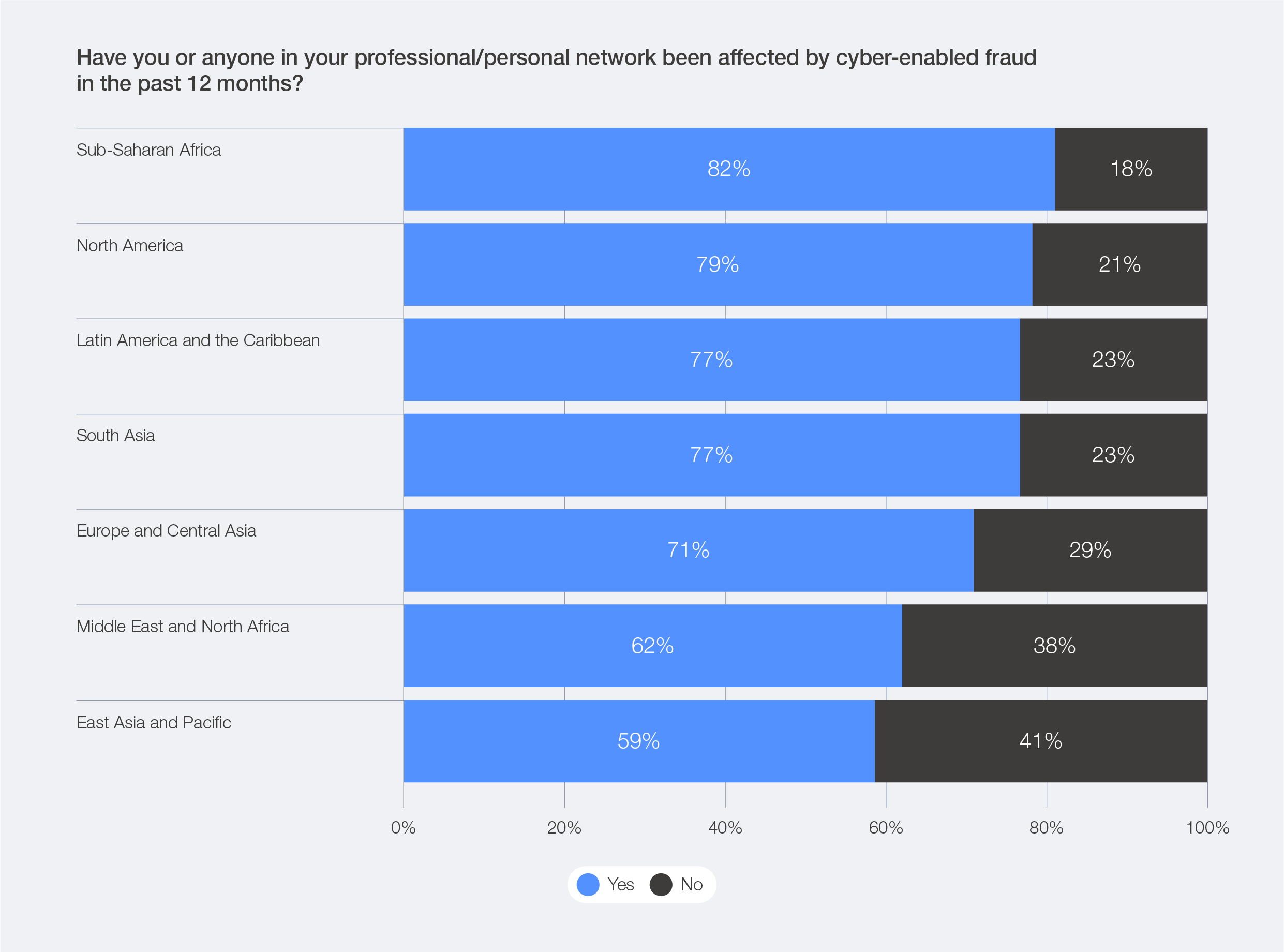
Cyber-enabled fraud continues to grow in scale, taking a heavy toll on individuals and organizations around the world. According to the Global Cybersecurity Outlook survey data, 77% of respondents reported an increase in cyber-enabled fraud and phishing overall, while 73% claimed that they or someone in their network had been personally affected by cyber-enabled fraud. The three most common types of attacks reported are phishing (including vishing and smishing), payment fraud and identity theft.
Figure 21: Prevalence of cyber-enabled fraud (all respondents)

Globally, cyber-enabled fraud is reaching record highs, and sub-Saharan Africa leads the trend, with 82% of respondents reporting exposure to digital scams, followed by North America, with 79% of respondents. Cyber-enabled fraud poses a pervasive societal threat, undermining trust and security across all demographics – from corporate leaders to households and vulnerable populations.
Figure 22: Prevalence of cyber-enabled fraud across regions
Global efforts to combat cyber-enabled fraud
To tackle fraud, global efforts to combat cyber-enabled crime are gaining momentum. The United Nations Office on Drugs and Crime (UNODC) and the International Criminal Police Organization (INTERPOL) are co-organizing the Global Fraud Summit in March 2026. The summit will serve as a platform to galvanize international action by fostering high-level dialogue, political and law enforcement commitments, and effective cross-sector collaboration.17 This high-level discussion comes after several significant operational disruptions of cybercrime networks across South-East Asia, Africa and Europe in 2025. Civil society and the private sector are also coordinating efforts. The Global Anti- Scam Alliance (GASA), for instance, is leveraging the Global Signal Exchange to enhance real-time insights into the supply chains that enable scams.18
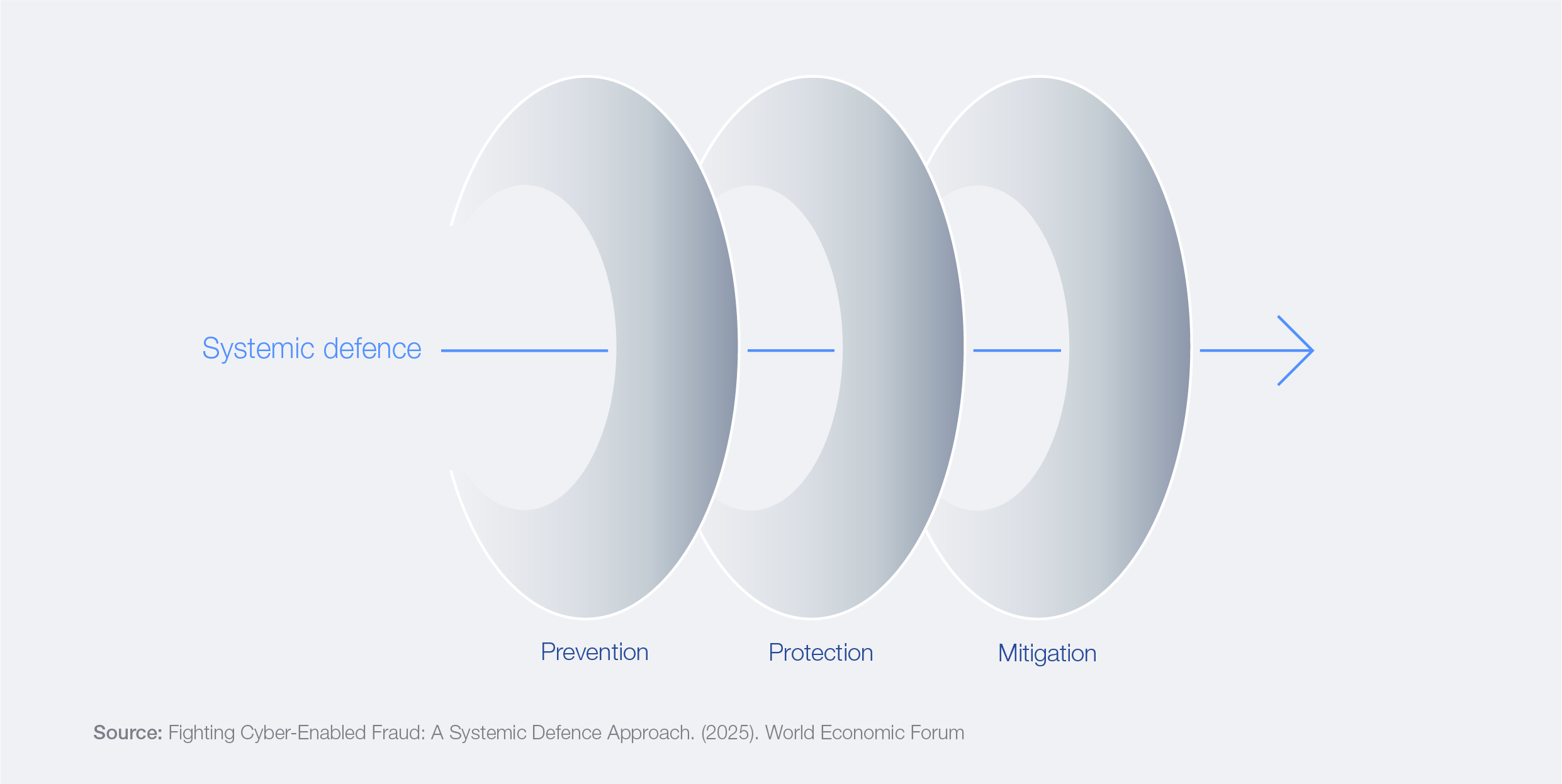
In parallel, the World Economic Forum’s Partnership Against Cybercrime (PAC), in collaboration with the Institute for Security and Technology (IST), has published the white paper Fighting Cyber-Enabled Fraud: A Systemic Defence Approach.19 The paper calls on stakeholders to act across three pillars – prevention (structurally reducing abuse before it occurs), protection (embedding user safety by default) and mitigation (enabling rapid, collective response) – outlining a shared responsibility model designed to disrupt cyber-enabled fraud at scale (see Figure 23).
Together, these initiatives reflect a growing international commitment to strengthen systemic defences and address cyber-enabled fraud through coordinated global action.
Figure 23: Systemic defence framework
AI-enabled cybercrime
Recent developments in genAI are lowering the barriers to executing phishing attacks while simultaneously increasing their sophistication and credibility. Criminal actors are exploiting genAI to automate and scale social engineering efforts, producing realistic phishing emails, deepfake audio and video, and falsified documentation capable of evading conventional detection systems and human scrutiny.
Furthermore, AI models trained on compromised or breached datasets are being weaponized to enhance targeting precision, replicate authentic communication styles and manipulate human trust with greater effectiveness. These capabilities represent a substantial evolution in the threat landscape, requiring more advanced and adaptive defence mechanisms. As such, this also amplifies digital safety risks for vulnerable groups, including children and women, who are increasingly targeted through impersonation, grooming and synthetic intimate-image abuse.
By enabling the translation and localization of social engineering tactics, these tools make impersonations more culturally authentic and convincing – helping attackers gain initial access to victims’ systems or earn their trust. As a result, criminal networks that once focused primarily on speakers of widely used languages can now effectively target new populations in regions that were previously less vulnerable to such scams. This expansion also accelerates the spread of AI-assisted mis/disinformation, complicating efforts by platforms and regulators to maintain information integrity and safeguard users from coordinated manipulation.
The rapid rise of deepfake technology is creating new challenges for organizations, governments and societies. In Indonesia, a wave of deepfake scams, featuring fabricated videos of President Prabowo Subianto promising financial aid, has swindled Indonesians across 20 provinces.20 In Ireland, a malicious deepfake video falsely depicting presidential candidate Catherine Connolly announcing her withdrawal from the race sparked outrage and an official complaint to the Electoral Commission.21
As AI accelerates the scale and sophistication of cyber-enabled harm, increasing the cybersecurity and safety of users becomes a core pillar of resilience, requiring stronger verification standards, cross-platform coordination, safeguards for vulnerable groups and tools that help users navigate an increasingly challenging information environment.22
While genAI is currently used primarily to enhance social engineering and reconnaissance, the emergence of autonomous AI agents capable of executing full-scale attacks signals a potential turning point. In November 2025, Anthropic disclosed a cyber espionage operation that demonstrated the unprecedented use of AI across the entire attack life cycle – from reconnaissance and exploitation to data exfiltration. The incident showed how AI-enabled threat campaigns are rapidly evolving towards greater automation and independence. It also represented the first confirmed case of agentic AI gaining access to high-value targets, including major technology companies and government agencies.23
The changing architecture of cybercrime
The Global Cybersecurity Outlook 2025 highlighted the growing convergence between cybercrime and organized crime groups, noting that the cybercrime landscape has evolved from opportunistic activities to highly organized operations that increasingly mirror legitimate business practices. The commercialization of cybercrime, via cybercrime-as-a-service (CaaS) platforms, continues to lower entry barriers and expand the scale, sophistication and impact of cyberattacks.
Over the course of 2025, a new shift has emerged in the structure and behaviour of cybercrime collectives. An increasing number of cybercriminals – particularly younger actors – are actively pursuing business disruption, along with visibility and status within the cybercriminal ecosystem.24 These groups frequently publicize their activities by announcing attacks, leaking stolen data or sharing screenshots on social media to showcase their capabilities. This culture of exposure has blurred the traditional boundaries between hacktivism, cybercrime and influence operations. Increasingly, groups frame their actions as activism to claim moral legitimacy and expand their online following, further complicating attribution and response efforts.
A persistent trend is the blurring of lines between cybercrime and nation-state activity. Cybercriminals often adopt and adapt the tools, tactics and procedures of state actors, once these become publicly known. Conversely, some nation-states mask their involvement by collaborating with or attributing operations to criminal groups, to maintain plausible deniability – or leverage the capabilities of these actors to advance their own strategic objectives, often in exchange for turning a blind eye to their illicit activities.
Facing rapid innovation in tech combined with the transformative impact of AI, law enforcement cannot fight cybercrime in isolation. Protecting communities now depends on true multistakeholder cooperation. Only together can we stay ahead of criminals and uphold safety, rights and resilience for a secure digital future.
— Valdecy Urquiza, Secretary-General, INTERPOL
Collaboration against cybercrime
In 2025, there have been several developments in the fight against cybercrime, including the signing of the Convention against Cybercrime, adopted by the United Nations General Assembly in December 2024 after five years of negotiation.25 The Convention establishes the first universal framework for investigating and prosecuting offences committed online – from ransomware and financial fraud to the non-consensual sharing of intimate images. Additionally, public–private collaboration has enabled law enforcement agencies to carry out several successful cybercrime takedowns (see Box 3).
Box 3: Disrupting cybercrime through multistakeholder collaboration
Law enforcement agencies are enhancing their cross-border coordination and intelligence-sharing capabilities, increasingly supported by expert insights from the private sector and international partnerships.
Some notable operations in 2025 include:
– Operation Serengeti 2.0: INTERPOL coordinated this operation with 18 African countries and the United Kingdom to tackle ransomware, online scams and business email compromise; it led to 1,209 arrests and the recovery of $97.4 million. The operation was strengthened by collaboration with the private sector and nongovernmental collaborations, such as the World Economic Forum-hosted Cybercrime Atlas.26
– Operation Secure: Led by INTERPOL, in coordination with law enforcement agencies across 26 countries and private-sector partners, the operation, focused on infostealer malware, dismantled 20,000 malicious IP addresses and domains, seized 41 servers and resulted in 32 arrests. These INTERPOL operations were conducted under the umbrella of projects funded by the United Kingdom’s Foreign, Commonwealth and Development Office.27
– Operation Endgame: Coordinated by Europol and Eurojust, with the support of international public and private partners, Operation Endgame dismantled malware infrastructure consisting of hundreds of thousands of infected computers containing several million stolen credentials.28
– Lumma Infostealer Disruption: Europol and Microsoft disrupted the Lumma malware ecosystem, affecting 394,000 infected machines and seizing 1,300+ domains.29
3.4 Cyber resilience is the key to safeguarding economic value
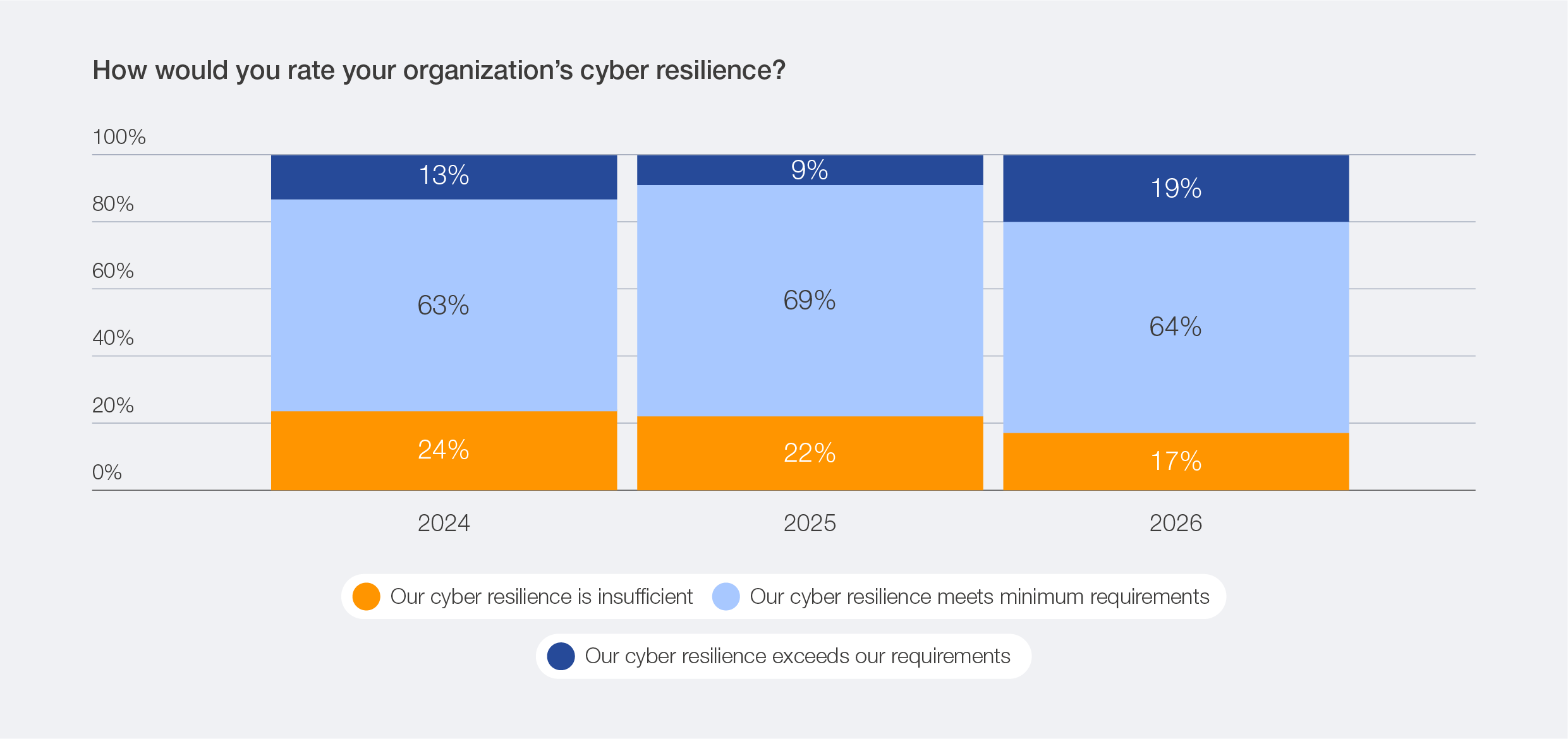
Cyber resilience underpins an organization’s ability to minimize the impact of significant cyber incidents on its primary business goals and objectives.30 Survey data shows increasing confidence in organizational cyber resilience. While 64% of organization report having met their minimum cyber resilience requirements, regardless of regional or sectorial variation (as further detailed in Section 3.6), only 19% claimed that cyber resilience exceeds their requirements. This is, however, a double-digit increase compared to 2025, when only 9% reported exceeding resilience requirements.
Figure 24: Year-over-year perception of cyber resilience
Nevertheless, cyber resilience remains under pressure. In 2025, a wave of cyberattacks struck organizations at every level – for example, in the United Kingdom alone, prominent retailers such as Marks & Spencer, Harrods and Co-op all suffered major operational disruptions and data losses due to ransomware attacks.31 These incidents underscore that, despite expressing growing confidence in cyber resilience, organizations are still facing major operational and reputational impacts from adversaries that are adapting rapidly.
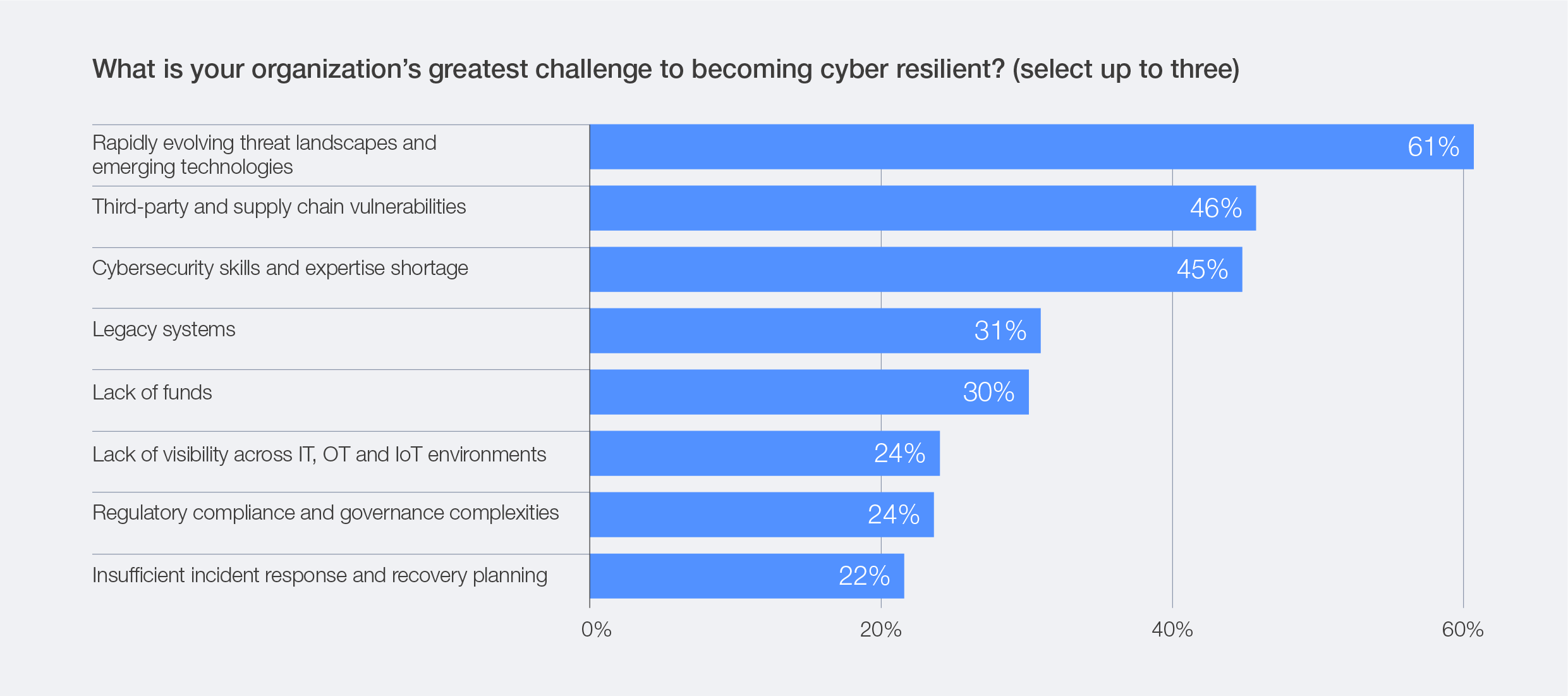
Against this backdrop, the top three reported challenges to strengthening cyber resilience, according to survey data, include: the rapidly evolving threat landscape and emerging technologies (61%); third-party and supply chain vulnerabilities (46%); and cyber skills and expertise shortages (45%).
Figure 25: Greatest challenges to cyber resilience for organizations
Legacy risks in a rapidly evolving landscape
Organizations are under pressure to adopt and prepare for new technologies while still struggling to secure legacy systems – 31% of respondents identified legacy infrastructure as one of their greatest challenges to achieving cyber resilience. Where technological innovation outpaces an organization’s capacity to adopt and upgrade its existing infrastructure, additional security controls often become necessary. While such measures support safe and secure operations across the organization, staying current in today’s rapidly evolving technological landscape inevitably involves accepting some residual risk.
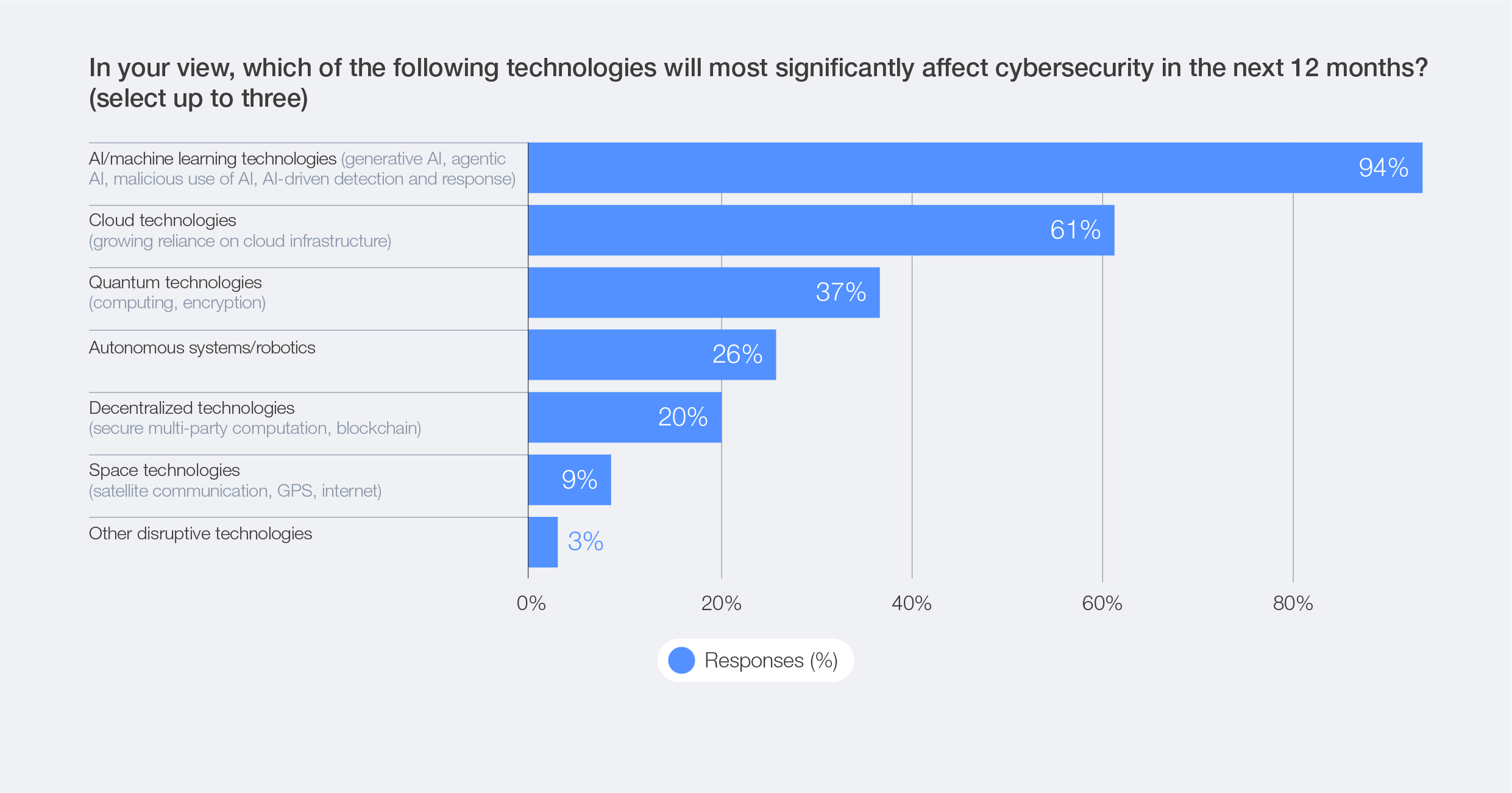
Over the years, successive waves of innovation cycles have caused organizations to accumulate a significant security debt, as speed and innovation were often prioritized over robust security measures. Indicative of this dynamic is the fact that survey respondents have ranked cloud technologies as the second-most significant technology expected to affect cybersecurity in the next 12 months. While many organizations are well advanced on their cloud journeys, this observation underscores that many of them are still deeply engaged with placing this topic high on their agenda.
Figure 26: Technologies with the greatest cybersecurity impacts in the next 12 months
From legacy to resilience: Enabling cyber-physical security
In today’s digital-industrial era, the boundary between IT and OT has all but disappeared. While strict air-gapped segregation of IT and OT systems used to be the norm in OT governance frameworks for years, contemporary advances in technology and expectations of connectivity between systems is making such practices untenable. Sectors such as manufacturing, energy, transportation and critical infrastructure systems now see IT and OT systems increasingly converge, driving efficiencies and innovation but also needing to apply more advanced segmentation to control risk exposure.
Many industrial environments remain ill-equipped for the speed and complexity of modern threats. OT systems are typically averse to rapid modernization due to their close integration with core business functions and their typically long investment horizons. Survey data reveals that, despite growing awareness, governance practices around OT remain inconsistent and often siloed within operational teams.
Figure 27: Best practices in OT governance
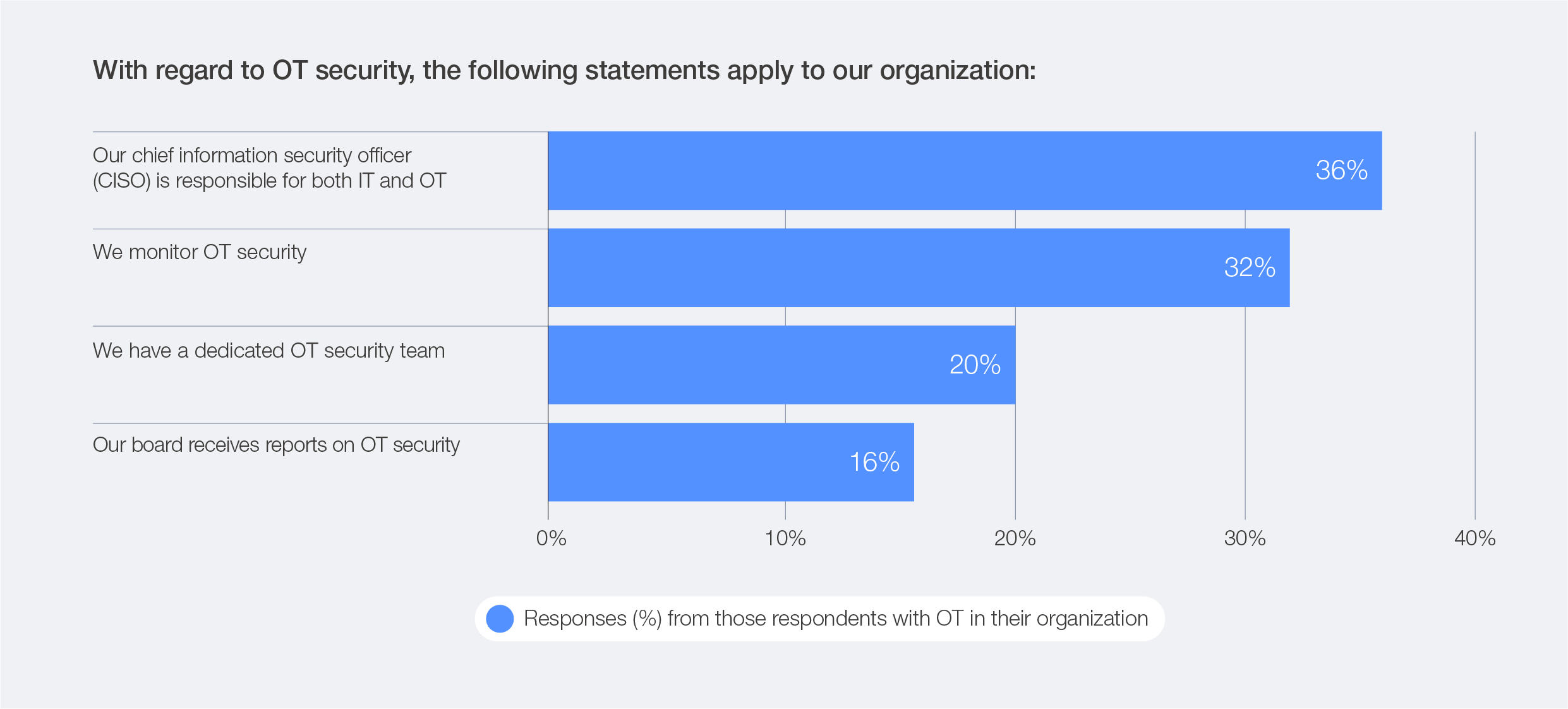
Only 16% of organizations with industrial environments report OT security issues to their boards, and just 20% maintain dedicated security teams. Meanwhile, 32% of organizations actively monitor OT systems with specific security tooling, yet in only 36% of the cases is the CISO directly responsible for OT security.
These findings indicate that OT protection is still mainly a priority for industrial environment specialists, and that bridging cultural gaps between IT and OT environments is paramount to mitigating the increasing cybersecurity risks. The lack of board-level oversight not only delays investment but also limits enterprise-wide understanding of risk exposure. This governance gap poses systemic implications: as is the case with IT, when disruptions in industrial systems similarly occur their effects cascade far beyond a single organization – to suppliers, partners and even national economies.
Cyber regulations in an era of fragmentation
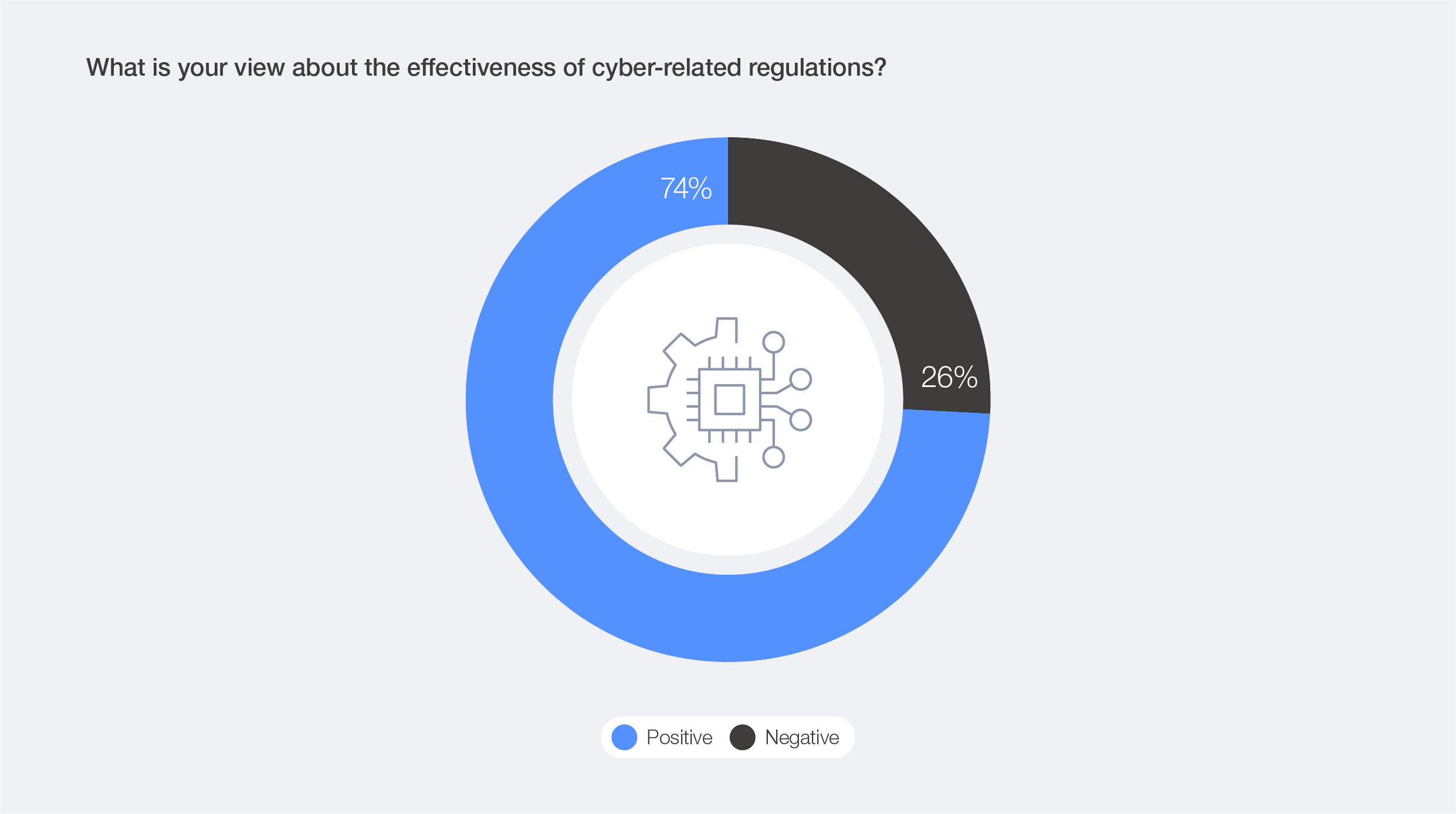
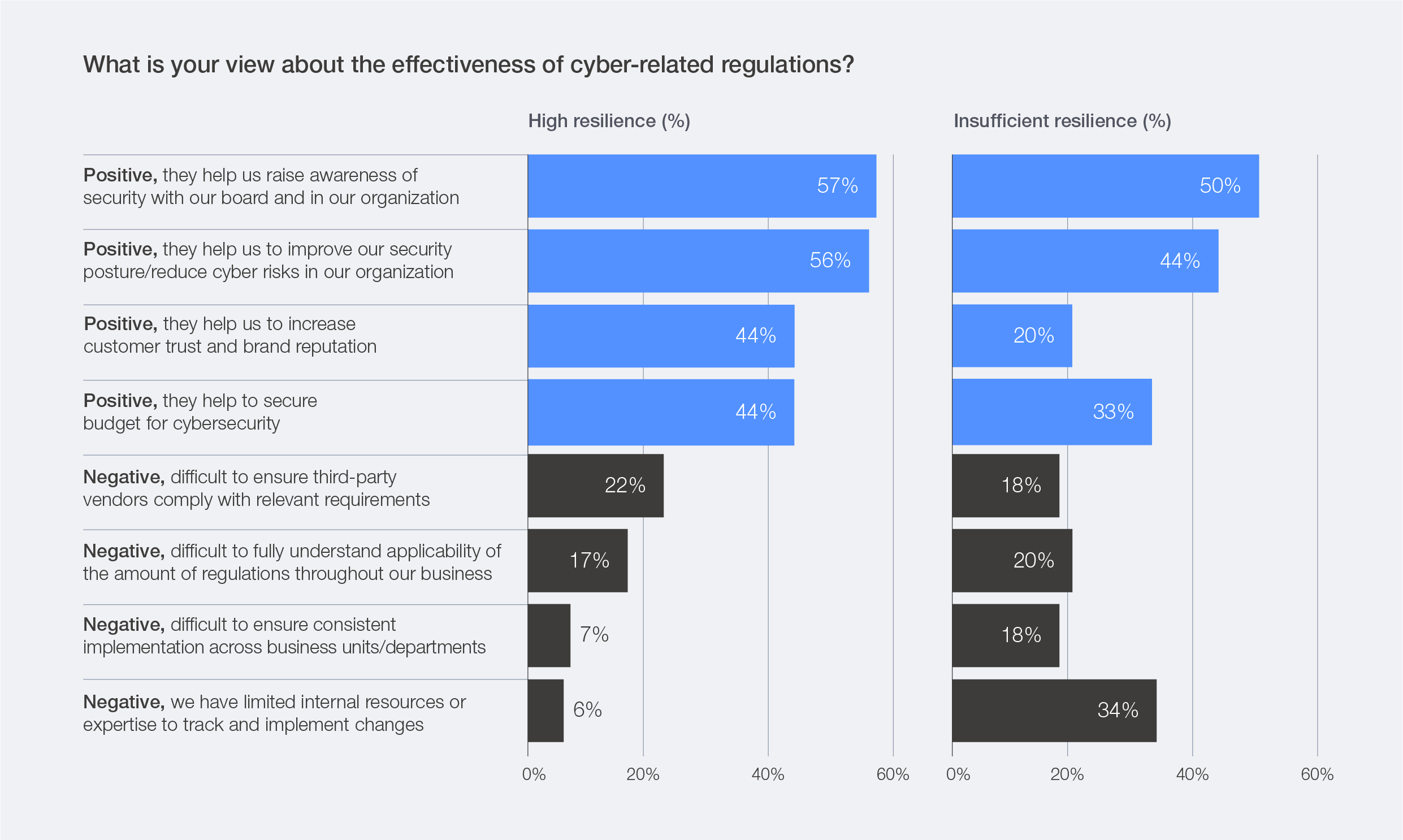
As nations strive to limit the exposure of their (digital) economies to global cyber challenges, the variation of approaches has added a new layer of complexity to the organizations that try to navigate a patchwork of regulations. The proliferation of cybersecurity and technology regulations globally reflects an accelerating effort to codify trust and accountability in the digital domain. However, these developments also highlight how regions are advancing at different speeds and with differing priorities, leading to a patchwork of obligations that can be difficult for multinational organizations to reconcile. Security leaders globally continue to recognize the value of regulatory frameworks in strengthening the cybersecurity ecosystem. This year’s survey found that 74% of respondents hold a positive view of the effectiveness of cyber-related regulations.
Figure 28: Perceived effectiveness of cyber-related regulations by all respondents
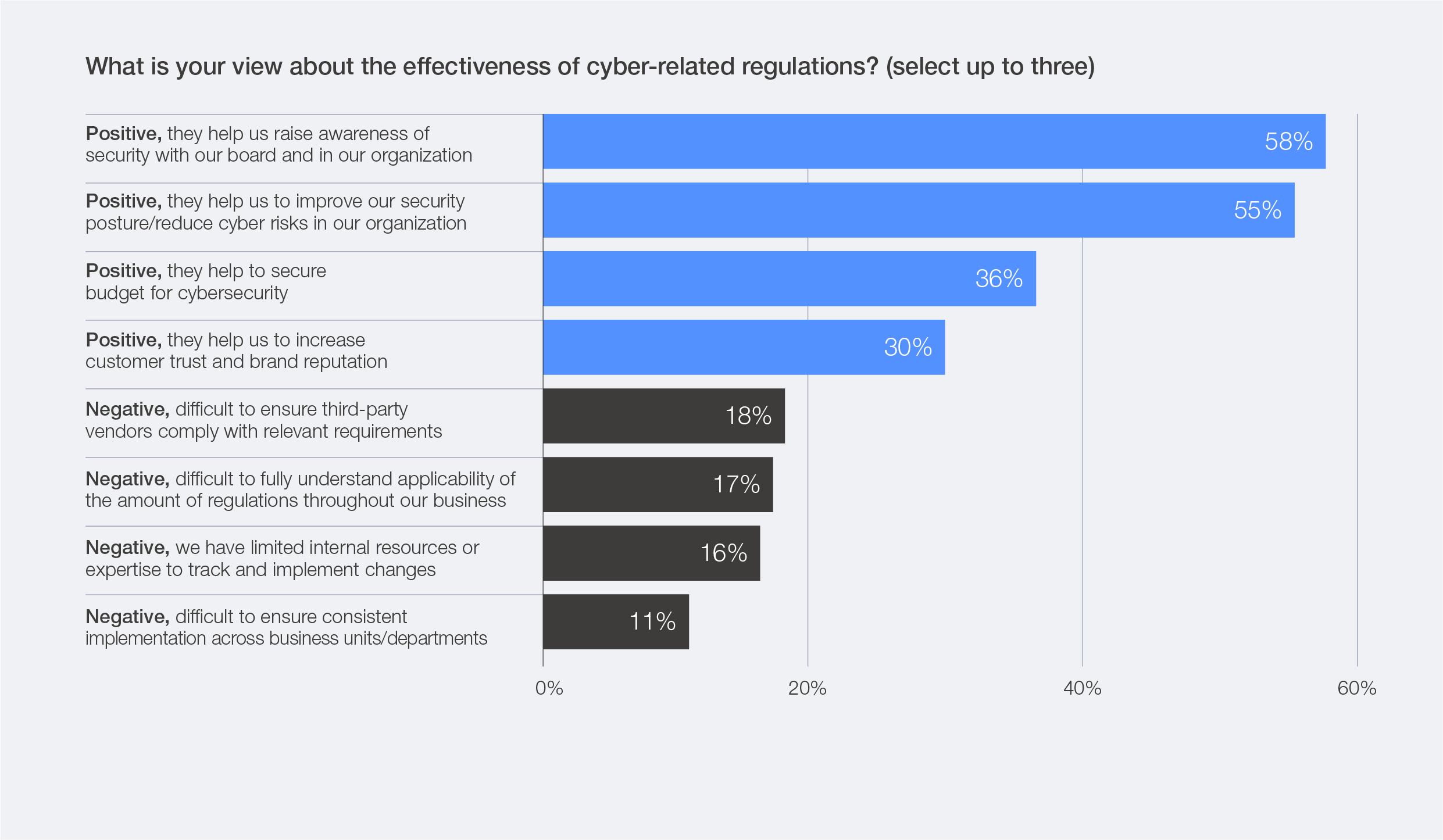
Practitioners most frequently note that these regulations help CISOs raise cybersecurity awareness at the board level (58%) and drive tangible improvements in overall security posture (55%). At the same time, 18% of respondents cited challenges in ensuring that third-party vendors comply with diverse requirements, while others pointed to difficulties in fully understanding the applicability of regulations across business units and to limited internal resources and expertise (16%).
Figure 29: Sentiment towards cybersecurity regulations
While the overall view on the benefits of regulations is largely positive, respondents based in markets where such regulations are more mature, such as Europe and North America, face greater difficulty in applying them consistently across borders. This is reflected in the fact that survey results reveal a slightly lower perception of the actual effectiveness of cyber-related regulations – 30% in Europe and 29% in North America – possibly reflecting the fact that more advanced regulatory environments can also introduce greater complexity and compliance burdens.
In a context of heightened geopolitical volatility and digital fragmentation, regulation thus serves as both a stabilizing force and a shared language for resilience – even as the contours of sovereignty and coordination continue to evolve.
Figure 30: Sentiment towards cybersecurity regulations, by region
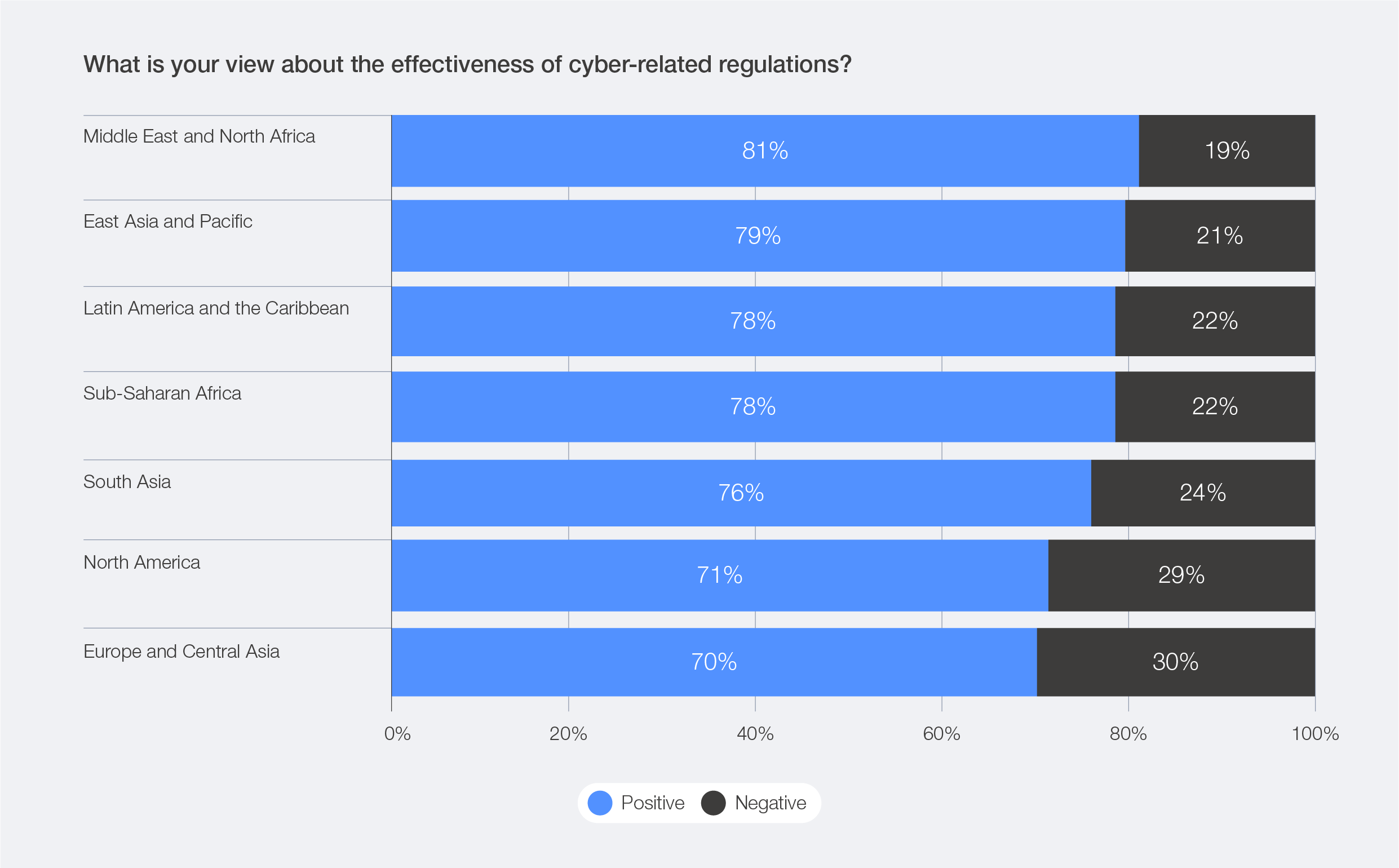
Figure 31: Hallmarks of resilient organizations
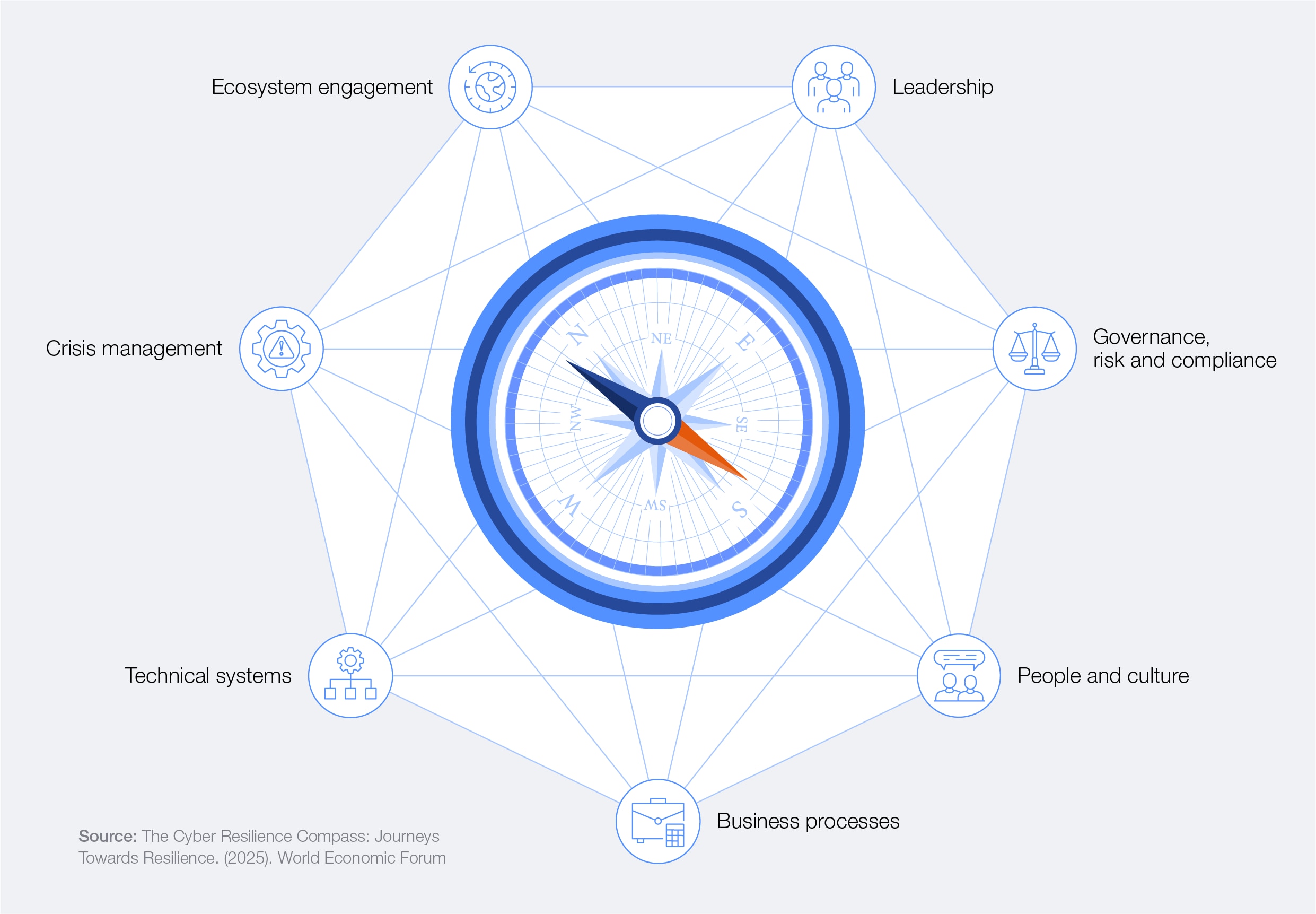
The Cyber Resilience Compass32 is a collaborative framework that captures and shares proven frontline practices to help organizations strengthen their cyber resilience. It structures these practices into seven interrelated categories – leadership; governance, risk and compliance; people and culture; business processes; technical systems; crisis management; and ecosystem engagement.
The Global Cybersecurity Outlook 2026 survey data demonstrates that highly resilient organizations exemplify these front-line practices:
Table 4: Hallmarks of cyber-resilient companies
Leadership
Resilient organizations demonstrate strong board engagement in cybersecurity. Some 99% of respondents from highly resilient organizations report board involvement in this area. Among these, 52% indicate that board members receive regular cybersecurity updates, 48% report that board members are actively engaged with the cybersecurity function, and 45% state that their board has a clearly defined role in overseeing cybersecurity.
Figure 32: Board engagement gaps, across organizational resilience levels
The World Economic Forum Centre for Cybersecurity’s latest white paper, Elevating Cybersecurity: Ensuring Strategic and Sustainable Impact for CISOs,33 explains that in order to strengthen resilience in an era of systemic cyber risk, organizations must empower CISOs and senior leaders to translate cybersecurity priorities into strategic business action.
Governance, risk and compliance
When viewing governance, risk and compliance from a regulatory perspective, survey data shows that those organizations reporting high levels of resilience tend to express more favourable views on the effectiveness of regulations. Some 44% of highly resilient organizations underscore that regulations help them increase customer trust and brand reputation, compared to 20% of those that classify themselves as being insufficiently resilient. Conversely, insufficiently resilient organizations are more likely to report limited resources to track and implement changes to regulations (34%).
Figure 33: Sentiment on regulations, by organizational resilience level
People and culture
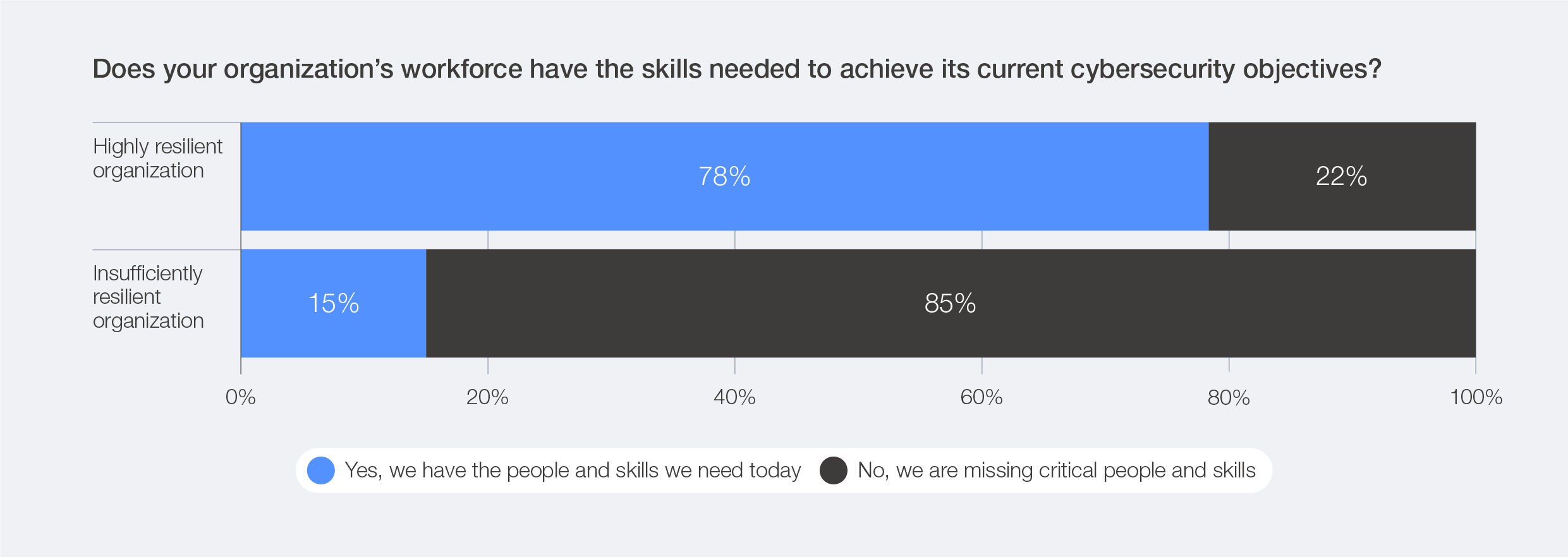
Only 22% of highly resilient organizations report lacking the necessary workforce to achieve their cybersecurity objectives – a stark contrast to the 85% of insufficiently resilient organizations that face this challenge.
Business processes
Defined business processes that support cybersecurity posture are a key characteristic of resilient organizations. Survey data indicates that 76% of highly resilient organizations involve their security function in the procurement process, compared to just 53% in insufficiently resilient organizations.
Technical systems
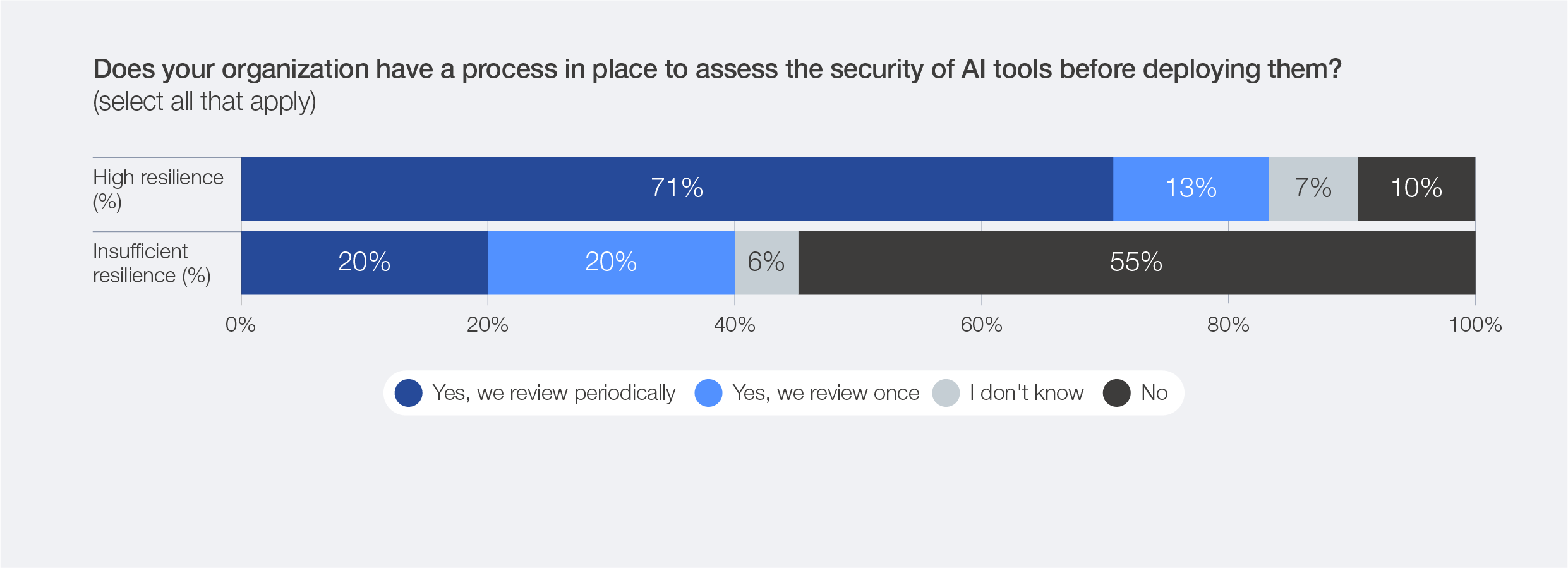
Resilient organizations take a structured approach to designing, deploying and maintaining technical or digital systems: 44% of highly resilient organizations monitor OT security, compared to only 9% of insufficiently resilient ones. Additionally, 71% of highly resilient organizations regularly review the security of their AI tools, compared to only 20% of insufficiently resilient organizations.
Figure 34: AI security assessment, by organizational resilience level
Crisis management
Resilient organizations have crisis plans and playbooks in place and regularly conduct ecosystem-wide exercises. According to survey data, 44% of highly resilient organizations simulate cyber incidents with their ecosystem partners, compared to only 16% of insufficiently resilient ones. They are also significantly better prepared for incident response and recovery – only 15% of highly resilient organizations report insufficient planning in this area, versus 37% of less resilient organizations.
Ecosystem engagement
Highly resilient organizations are more proactive in engaging their entire ecosystem: 53% share cybersecurity information with partners (compared to 31% of insufficiently resilient organizations); 74% assess the security of their suppliers (versus 48%); and 44% map their ecosystem and evaluate partners’ exposure to risk (versus 23%).
Figure 35: Organizational supply chain risk, by resilience level
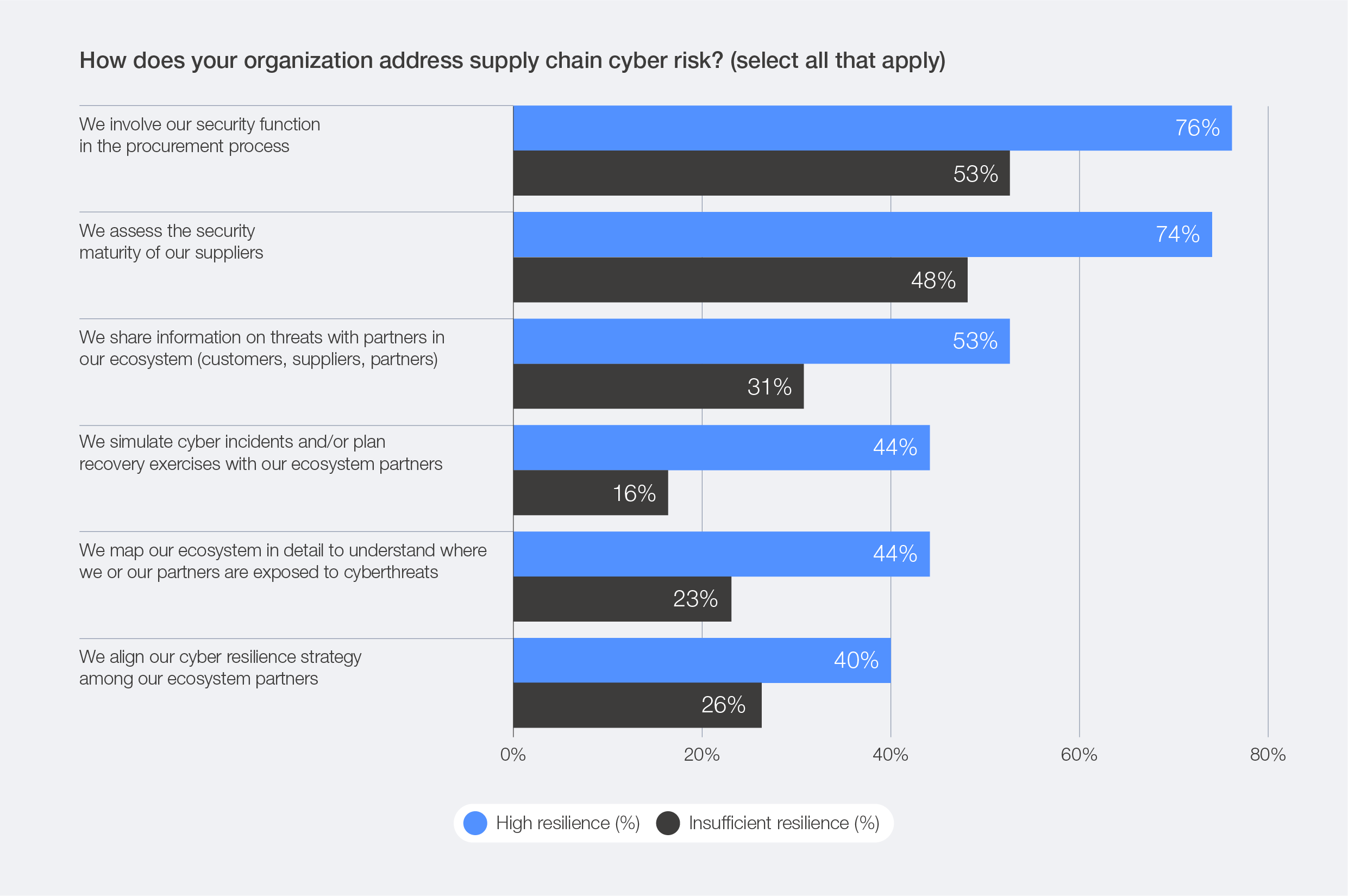
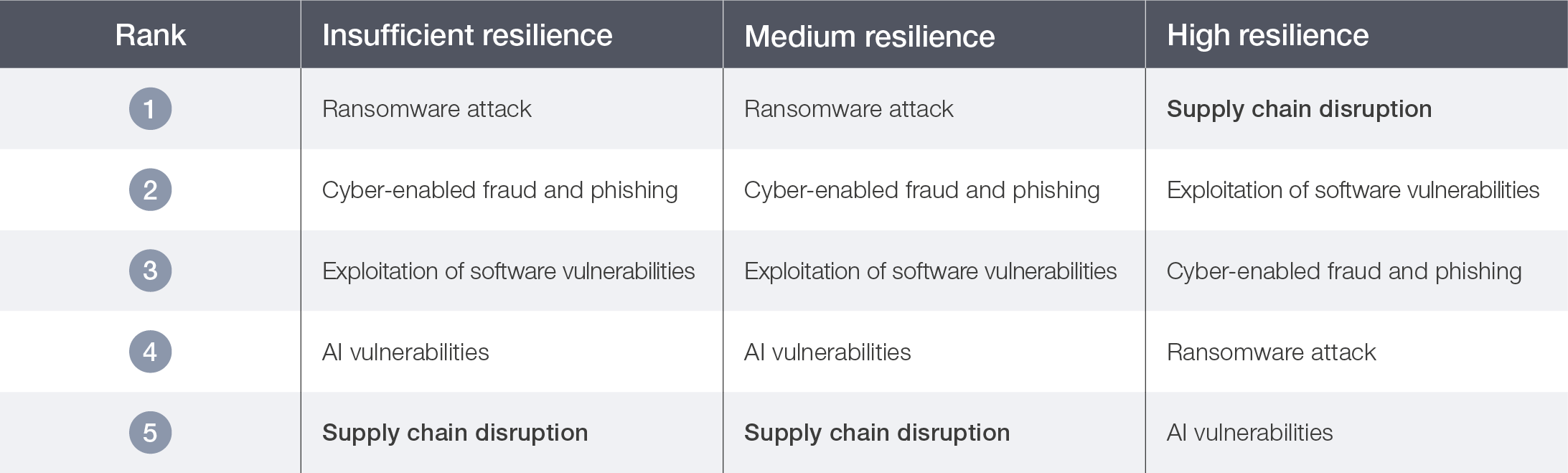
Moreover, highly resilient organizations demonstrate a broader risk perspective, focusing not only on their internal posture but also on external dependencies across their ecosystem. Survey data shows that supply chain exposure ranks as the top cyber risk concern among high-resilience organizations, whereas moderately resilient and insufficiently resilient organizations ranked it only fifth (see Table 5). This suggests that more mature organizations are increasingly recognizing that their resilience depends as much on the strength of their partners as on their own defences.
Figure 36: Organizational resilience barriers, by resilience level
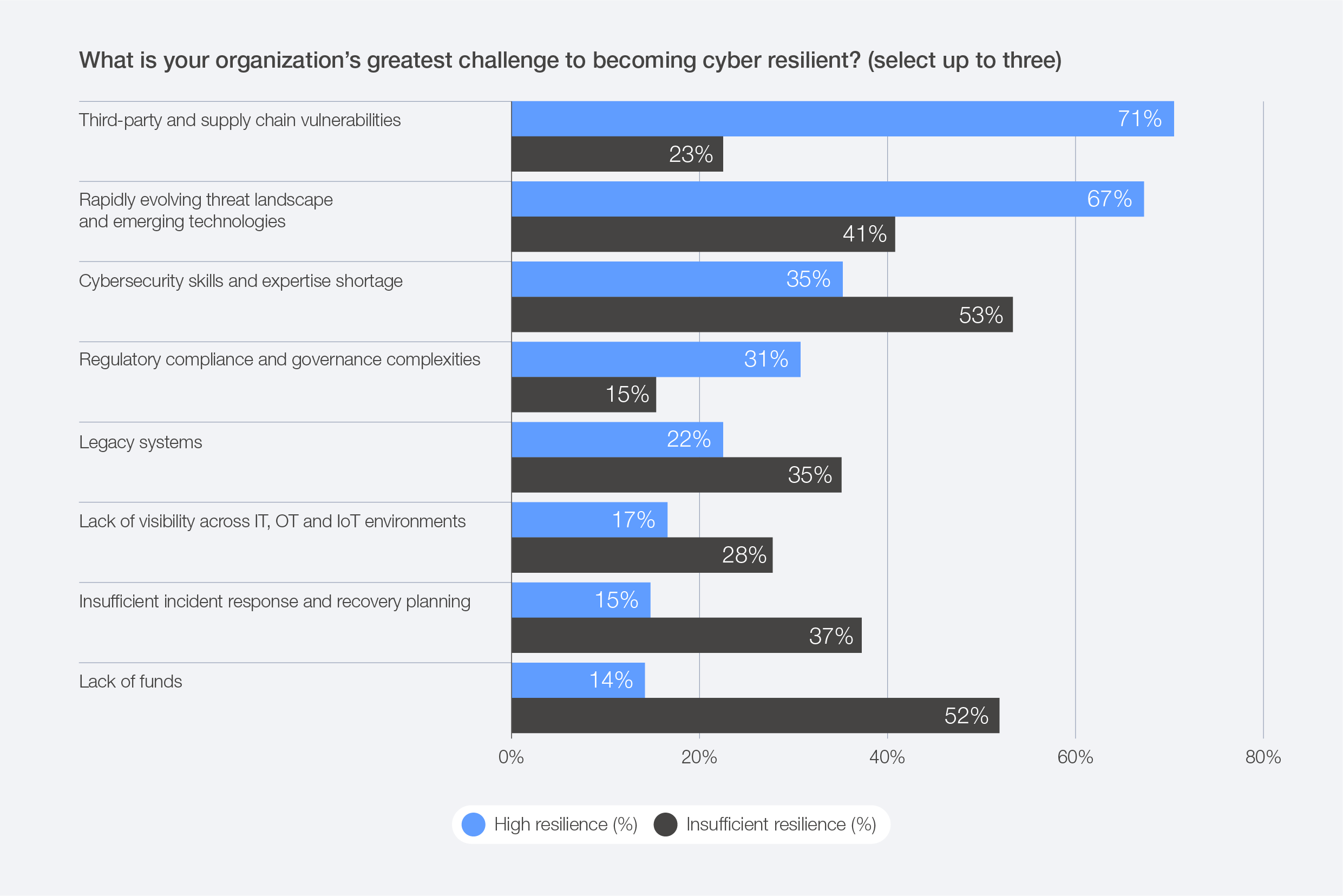
Table 5: Ranking of cyber risk concerns, by organizational resilience level
With AI doubling in compute every three months or so, the risks of technology-enabled sophisticated cybercrimes have never been greater in human history. No matter how high your walls, every business faces an elevated risk of being breached. As perpetually adaptive enterprises, our focus has to be on building strong resilience and recovery frameworks, so that we can get our businesses, societies and economies up and running rapidly after an incident has taken place. The businesses that thrive in the future will not be those that have never been hit by cyber hacks or crimes, but those which have built the strongest capability to recover from them.
— K. Krithivasan, Chief Executive Officer and Managing Director, Tata Consultancy Services
The economic dimension of cybersecurity
Cybersecurity is no longer just a technical issue; it is increasingly becoming a strategic economic priority. Decisions about how much to invest in protecting digital assets have become financial choices that shape an organization’s resilience, competitiveness and growth trajectory.
Recent cyberattacks have underscored how deeply cybersecurity is intertwined with the broader economic landscape, inflicting tangible financial damage on businesses and national economies alike. According to United Kingdom government research, the average significant cyberattack costs businesses nearly £195,000 ($250,000). Scaled nationally, this equates to an estimated £14.7 billion ($19.4 billion) in annual economic losses.34 Additionally, the World Bank notes that reducing major cyber incidents could boost gross domestic product (GDP) per capita by 1.5% in developing economies.35 Such figures illustrate why the financial drivers and consequences of cyber incidents are increasingly commanding the attention of leaders across both the public and private sectors.
In August 2025, Jaguar Land Rover – the United Kingdom’s largest automotive manufacturer – suffered a devastating cyberattack that brought production across its global operations to a halt for five weeks and affected more than 5,000 suppliers.36 The company faced direct financial repercussions, including £196 million ($260 million) in cyber-related costs and a nearly 25% drop in revenues to £4.9 billion ($6.5 billion).37 However, the wider UK economy absorbed an even greater shock, with an estimated £1.9 billion ($2.5 billion) in losses resulting from the disruption.38
This incident underscores several critical insights into the economics of cybersecurity. First, it highlights the importance of quantifying cyber risk and scenario-building to model the potential impact of cyberthreats, to drive adequate investments towards resilience. Second, it demonstrates the interdependence of supply chains, where disruptions in one actor can propagate across industries, amplifying risk and underscoring the need for sector-wide resilience strategies. Finally, it reinforces the vital role of public–private collaboration. The UK government’s £1.5 billion ($2 billion) loan guarantee to stabilize the supply chain exemplifies how coordinated responses and appropriate financial incentives are essential for managing systemic cyber risk and avoiding the need for such costly bailouts.39
Cybersecurity is not merely an IT function – it is a strategic business imperative and a cornerstone of national economic resilience. Beyond mitigating risk and preventing losses, it also serves as a driver of economic growth, fuelling innovation, job creation and competitiveness across industries. Investing in robust cyber risk management and resilience strategies not only safeguards corporate value and national stability but also strengthens the foundations of a secure and dynamic digital economy.
To explore this economic dimension of cybersecurity and inform policy and industry practices, in May 2025, the World Economic Forum and the Global Cybersecurity Forum established the Centre for Cyber Economics (CCE).40 The CCE aims to empower stakeholders with the knowledge, tools and capabilities needed to ensure that cybersecurity remains an integral pillar of economic growth.
Box 4: Advancing knowledge and understanding of the economic dimension of cybersecurity
Recognizing the growing imperative to address the economic dimension of cybersecurity, the World Economic Forum has partnered with the Global Cybersecurity Forum (GCF) to establish a new Centre for Cyber Economics (CCE) in Riyadh, as part of the Forum’s Fourth Industrial Revolution Network. Launched in May 2025, the centre is dedicated to advancing global understanding of the economic challenges and opportunities arising from an increasingly complex cyber landscape. Through cutting-edge research, cross-sector collaboration and evidence-based frameworks, the CCE aims to empower stakeholders with the knowledge, tools and capabilities to ensure cybersecurity remains an integral tenet of advancing economic growth. To that end, some of the core areas of the CCE will include the macroeconomic impact of cyberattacks and the quantification of cybercrime, as well as the implications of cybersecurity workforce shortages and skills gaps on economic growth.
3.5 Securing supply chains amid opacity and concentration risks
The digital supply chain is highly interconnected, with dependencies within and across industries that are often not clearly mapped. A breach or disruption of one supplier can cascade through the entire ecosystem, affecting production, operations and even other suppliers or customers. This complexity makes it difficult to assess and manage cyber risk effectively. Attacks on widely used software or service providers can have global and systemic impacts.
Such critical interdependencies were highlighted by the cyberattack affecting airports across Europe in September 2025, where a relatively minor breach targeting the check-in and boarding systems used by several major airport hubs caused a cascading disruption to airport operations, with flight delays and cancellations.41 Though the immediate damage was contained, the incident exposed the fragility of interconnected digital supply chains, leaving participants in focus groups for this report to reflect on how devastating a similar attack could be if directed at hospitals or other critical infrastructure.
Concerns about the resilience of supply chains against cyberattacks are continuing to worry business and cyber executives. This year’s survey data shows that 65% of large companies by revenue indicate third-party and supply chain vulnerabilities are their greatest challenge, which has risen from 54% in 2025.42
Figure 37: Large companies' greatest barriers to cyber resilience, 2025–2026
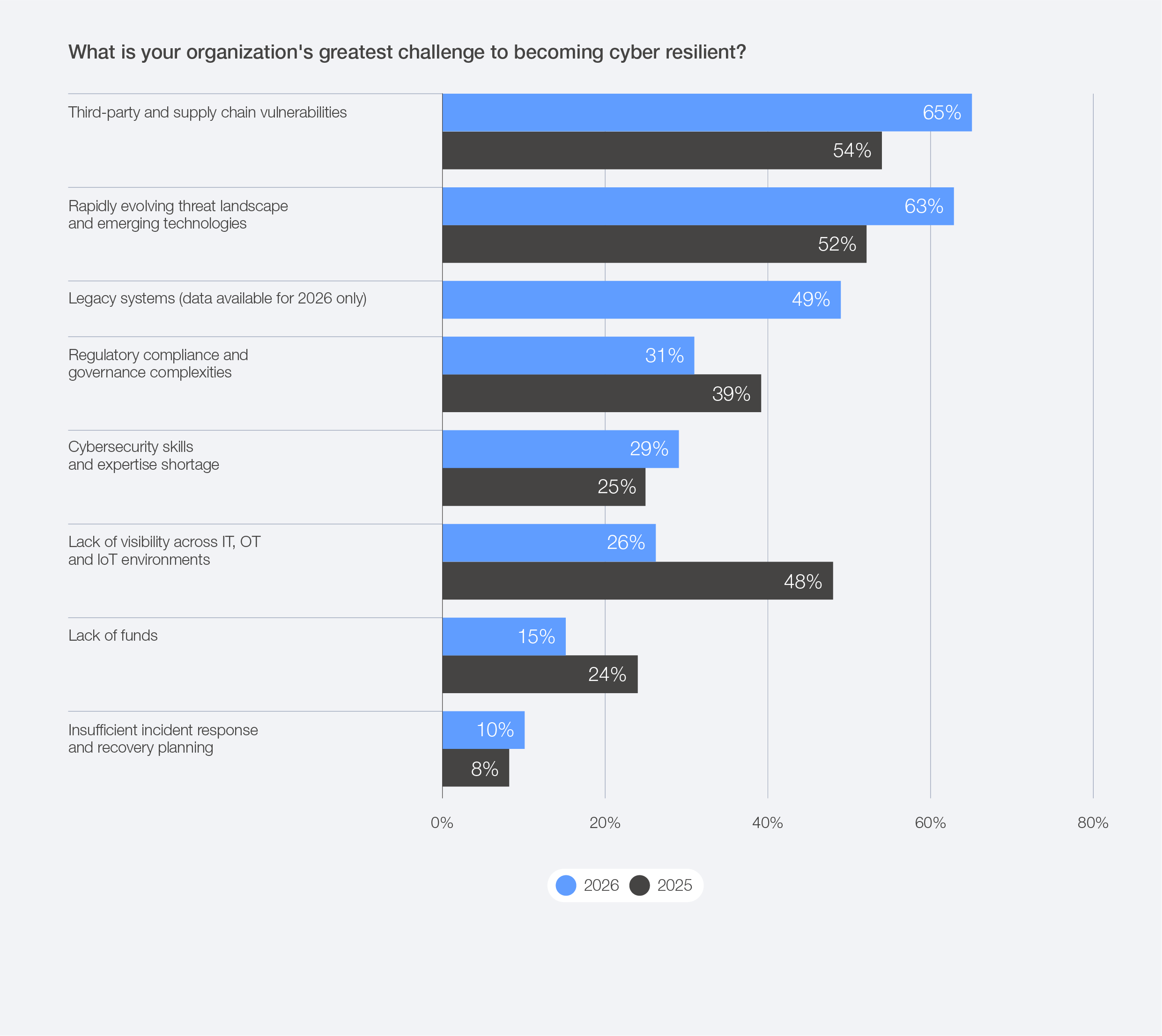
While supply chain vulnerabilities are worrying both business and cyber executives, Global Cybersecurity Outlook survey data shows that among a variety of concerns, CISOs tend to be more worried about the integrity of their external dependencies than CEOs.
Among cyber risks, supply chain vulnerabilities have ranked as the second-most concerning issue for CISOs for two consecutive years. CISOs are deeply attuned to the technological interdependencies that have evolved as organizations adopt new systems to support both operations and resilience, making them more sensitive to potential disruptions in business continuity.
The top supply chain risks in 2026
Organizations often lack direct control over the security practices of third-party vendors and suppliers. The Global Cybersecurity Outlook survey shows that inheritance risk – the inability to assure the integrity of third-party software, hardware and services – is the top supply chain risk, followed by visibility. Even when strong internal controls are in place, the weakest link is frequently a supplier or partner with lower cybersecurity maturity. This is especially acute with smaller suppliers, who may lack the resources or incentives to implement robust security measures.
Supply chain risks differ across industries. Overall, limited visibility emerges as the primary risk across industry clusters – especially for energy; financial services; manufacturing, supply chain and transportation; and materials and infrastructure – followed by inheritance risk.
Table 6: Ranking of top supply chain cyber risk
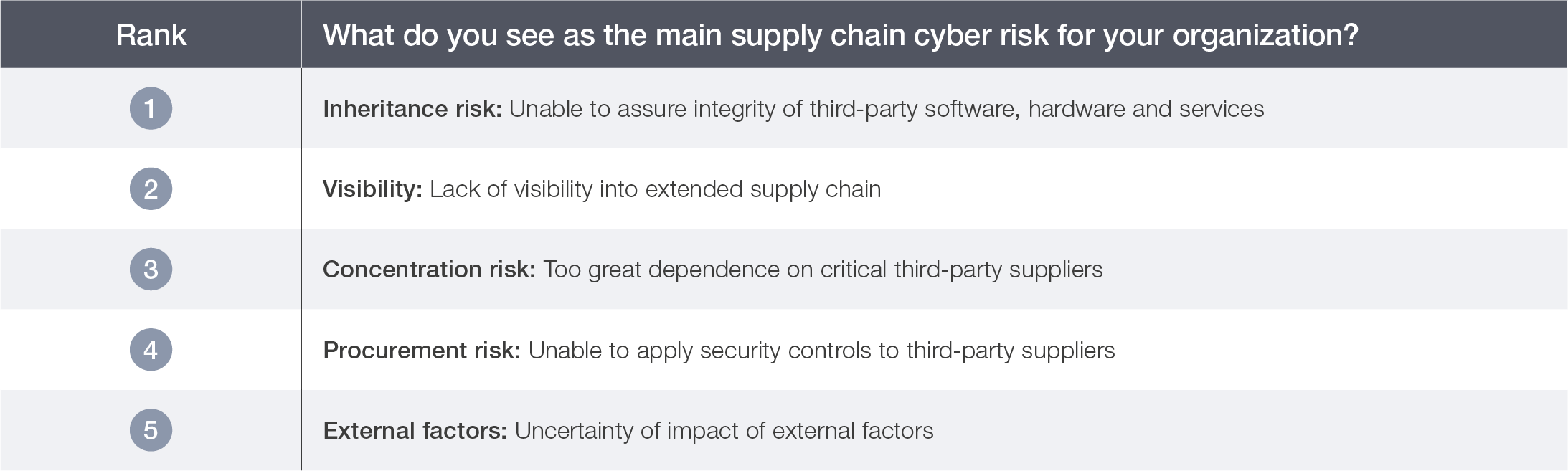
Table 7: Top supply chain risk, by industry
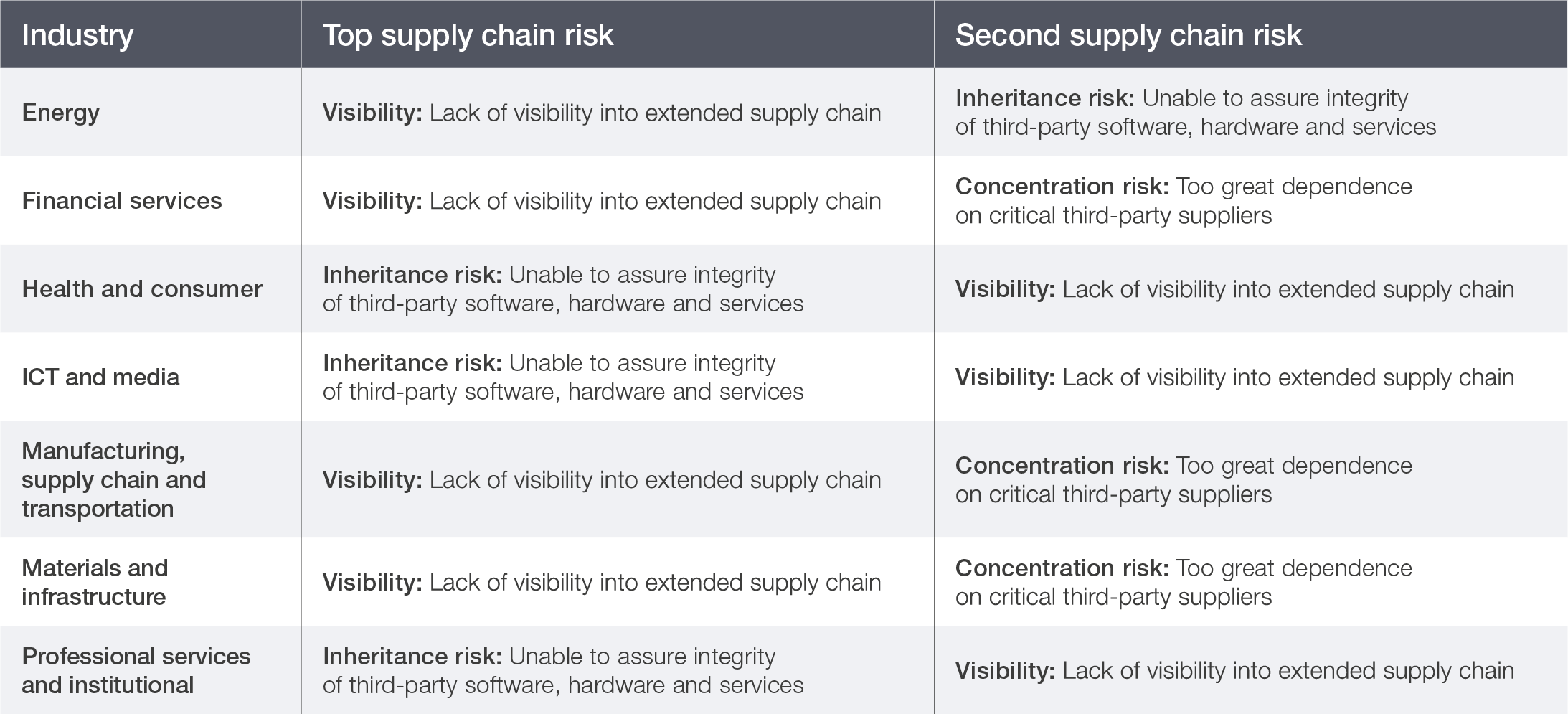
While the majority of organizations across industries evaluate the security maturity of their suppliers (66%) and involve the security function in procurement processes (65%), significantly fewer adopt more advanced resilience measures. Only 27% simulate cyber incidents or conduct recovery exercises, and a mere 33% comprehensively map their supply chain ecosystems to gain a deeper understanding of cyberthreat exposure and interdependencies. These survey results denote that supply chain risk management is often treated as a compliance checklist rather than as a dynamic, continuous process.
Existing regulations typically establish only a minimum-security baseline, which may be insufficient to address rapidly evolving threats. A key challenge lies in incentivizing both organizations and their suppliers to strengthen cyber resilience. Smaller vendors frequently lack the resources to implement robust security measures, while buyers may still prioritize cost and efficiency over security when choosing partners. This imbalance creates persistent exposures, as attackers tend to exploit the weakest links within the supply chain.
Cyber resilience is no longer confined to individual organizations; it depends on the strength of our entire ecosystem. By embedding cybersecurity across supply chains, sharing intelligence transparently and aligning public–private efforts, we can build a trusted digital foundation that supports innovation, stability and sustainable economic growth.
— Mohamed Al Kuwaiti, Head of Cybersecurity, United Arab Emirates Government
Figure 38: How organizations address supply chain risk
Adequate crisis management and recovery planning is essential to limit the impact of a cyber breach when it happens. For example, in the aftermath of the attack on Japanese beer manufacturer Asahi in October 2025, essential IT services were brought down, forcing staff to revert to pen and paper to maintain critical operations such as inventory tracking and manual checks of control data.43
Concentration of risk
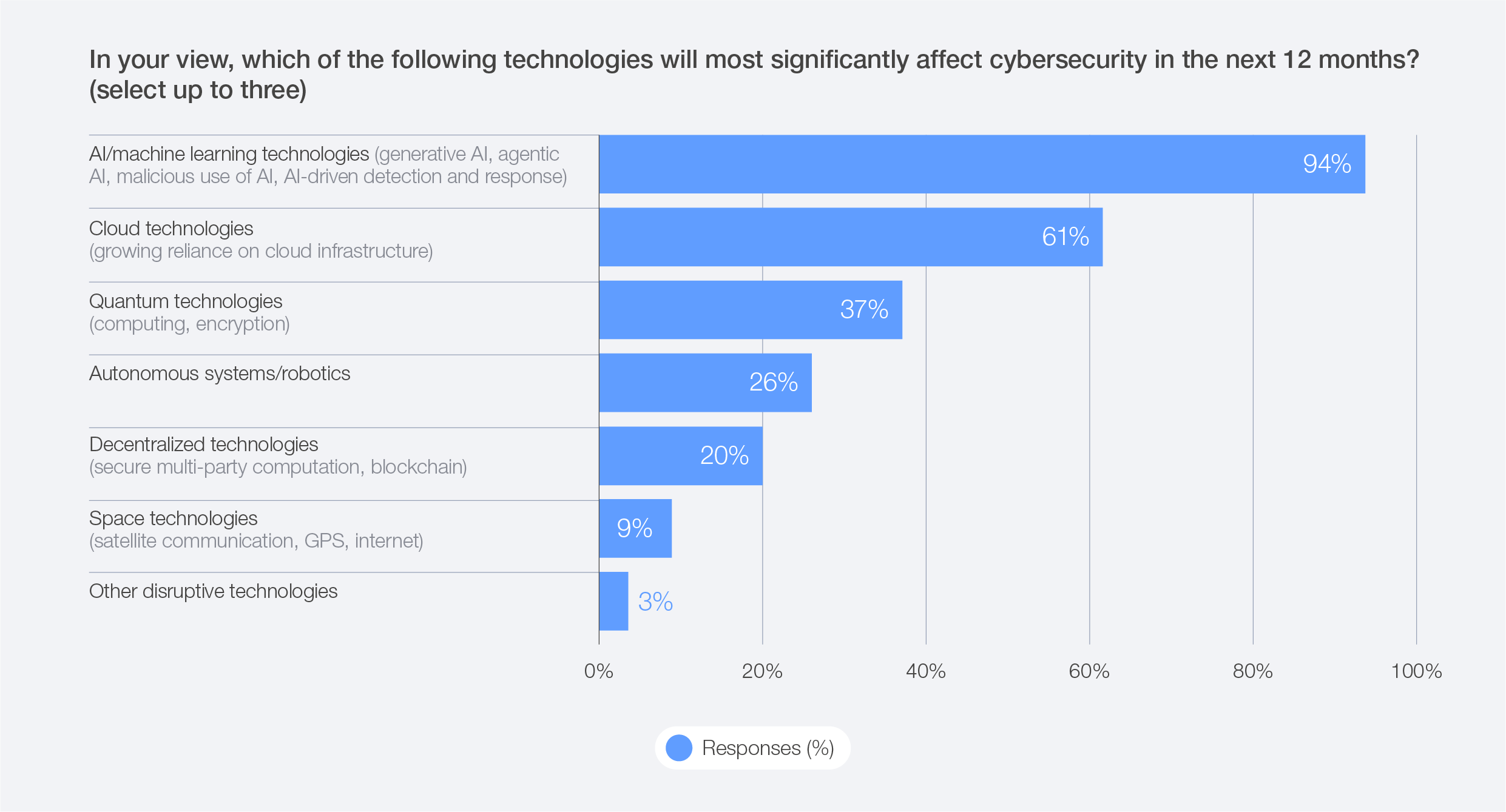
The growing dependency on a small number of critical digital providers remains a concern for cyber leaders, as it amplifies concentration risk across the ecosystem. A single vulnerability in a critical service provider may cause cascading impacts felt across the globe. The increasing use of internet of things (IoT) devices and cloud-based services is expanding the attack surface and introducing new vulnerabilities, especially when these technologies are integrated into supply chains or vendor ecosystems without adequate security controls. Survey data highlights this risk: cloud technologies are identified as the second most impactful technology for cybersecurity in 2026, after AI.
Figure 39: Technologies that organizations expect to most significantly affect cybersecurity in the next 12 months
Cloud providers have become critical enablers of modern ecosystems, yet they also represent concentrated points of dependency across organizations’ ecosystems. As digital supply chains rely more on an interconnected cloud environment, the boundaries become increasingly complex, creating governance and resilience challenges. While these platforms strengthen efficiency and connectivity, a single disruption or misconfiguration can cascade through the entire organization ecosystem, exposing how cloud and IoT Integration increase overall exposure.
In October 2025, a disruption occurred due to a misconfiguration in a Domain Name System (DNS) operated by Amazon Web Services (AWS), affecting thousands of organizations worldwide. Microsoft Azure cloud platform also experienced a global outage during the same month.44 Shortly after, in November 2025, Cloudflare also experienced an outage, disrupting many online services.45 While not cybersecurity issues, these events illustrate how provider-level incidents can generate broad downstream impacts across interconnected digital ecosystems.46
3.6 Drivers of cyber inequity in 2026
Cyber capacity across the global ecosystem remains uneven across industries and regions, influenced by differences in skills, resources and available digital infrastructure and governance frameworks. While certain organizations continue to invest in security, many others face challenges in sustaining even a baseline level of cybersecurity. This imbalance – described as cyber inequity – creates vulnerabilities that extend beyond individual entities, exposing entire interconnected supply chains to risk. The Global Cybersecurity Outlook 2025 examined this inequity through three key dimensions: small versus large organizations; developed versus emerging economies; and disparities across sectors.
The 2026 survey data reveals that perceptions of resilience levels still vary across regions. High degrees of confidence in resilience levels are expressed by respondents based in the Middle East and North Africa, while lower levels of resilience are expressed in Latin America and the Caribbean and sub-Saharan Africa. Despite rising confidence in cyber resilience overall, inequities persist between smaller and larger organizations.47 Survey data indicates that small organizations (by revenue) are twice as likely to experience insufficient resilience levels as large organizations. Similarly, across sectors, survey data reveals that the divide remains: NGOs report 37% insufficient resilience, and the public sector 23%, compared with just 11% in the private sector.
Figure 40: Regional levels of organizational cyber resilience
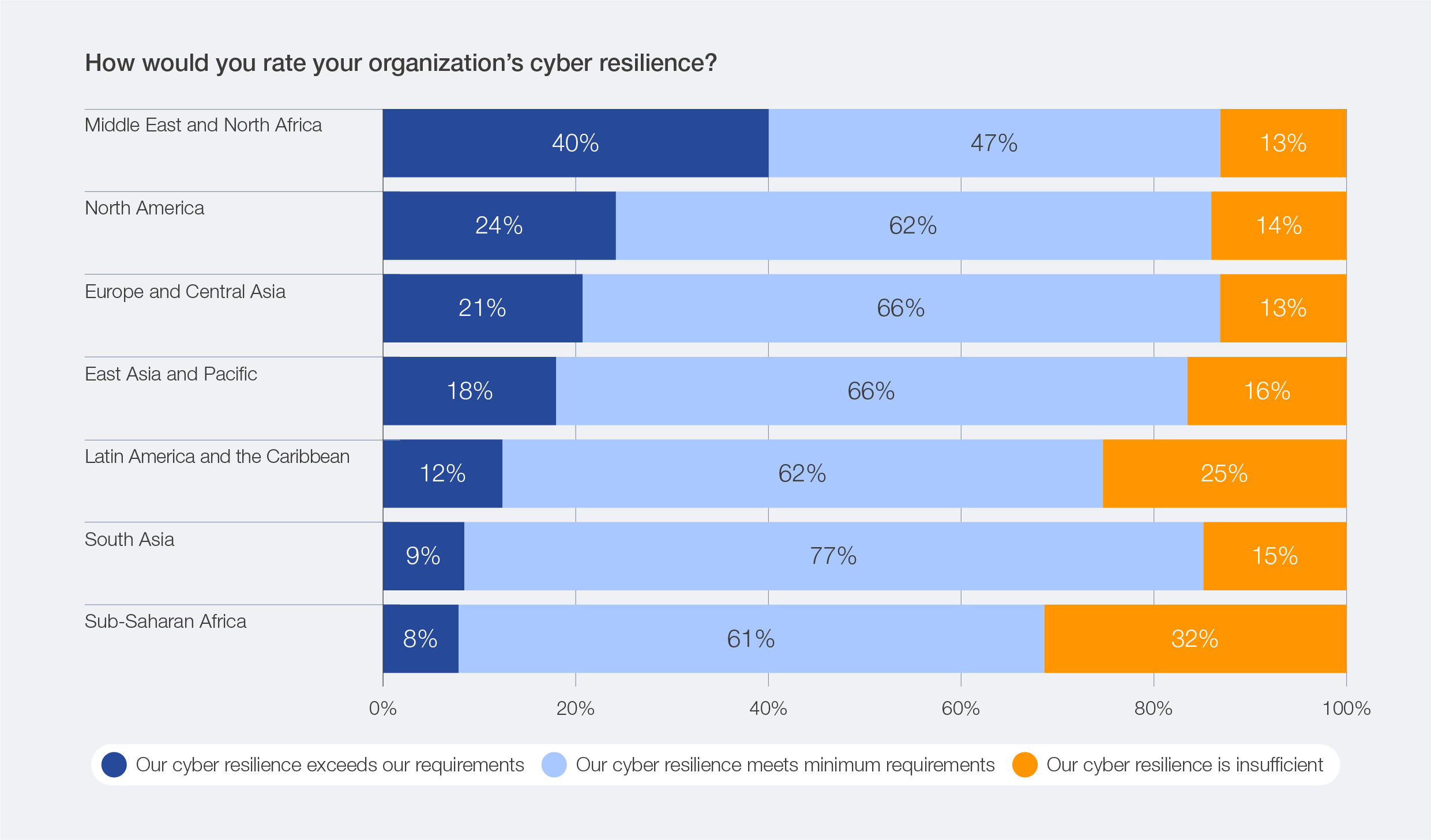
Figure 41: Cyber inequity across the public sector, private sector and NGOs
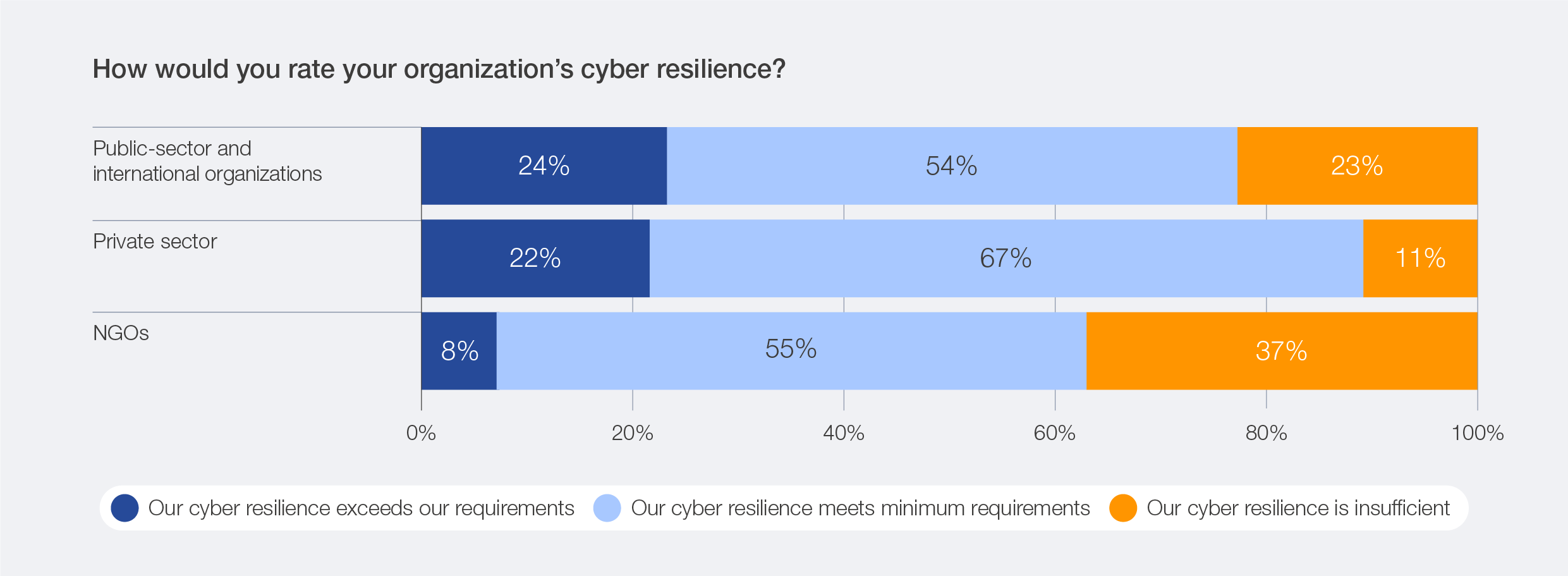
Cyber skills shortages as a key driver of inequity
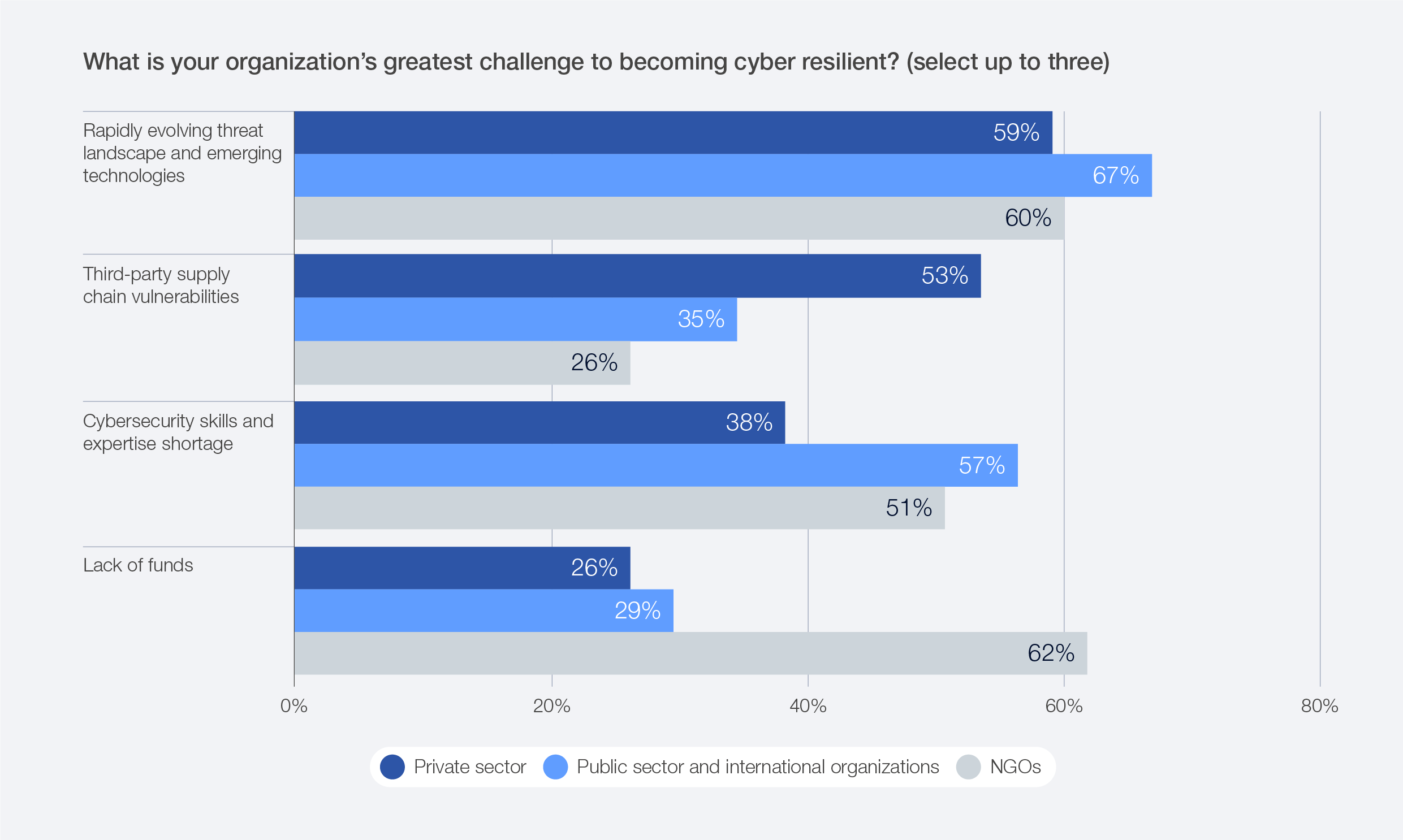
Cyber inequity is a multifaceted challenge, shaped by disparities in resources, capabilities and access across countries, sectors and organizations. While gaps in security governance frameworks, limited financial resources and unequal access to digital infrastructure all contribute to this imbalance, one factor stands out for its pervasive impact: the shortage of cybersecurity skills.
While the evolving threat landscape remains the foremost concern, the lack of cybersecurity expertise ranks as the second-most significant challenge – NGOs (51%) and the public sector (57%). When comparing small and large organizations, the data reveals a persistent divide: 46% of small organizations report a lack of cybersecurity skills and expertise, compared with 29% of large organizations.
Figure 42: Resilience challenges across sectors
Having adequate cybersecurity skills has emerged as a key differentiator between highly resilient and insufficiently resilient organizations. Among those reporting insufficient levels of cyber resilience, 85% also cited missing critical skills and people to fulfil cybersecurity objectives. By comparison, only 22% of highly resilient organizations viewed skills gaps as a significant challenge. According to the survey, the top three cybersecurity roles experiencing shortages are threat intelligence analysts, DevSecOps engineers, and identity and access management specialists.
Figure 43: Perceived resilience levels and cyber skills shortages
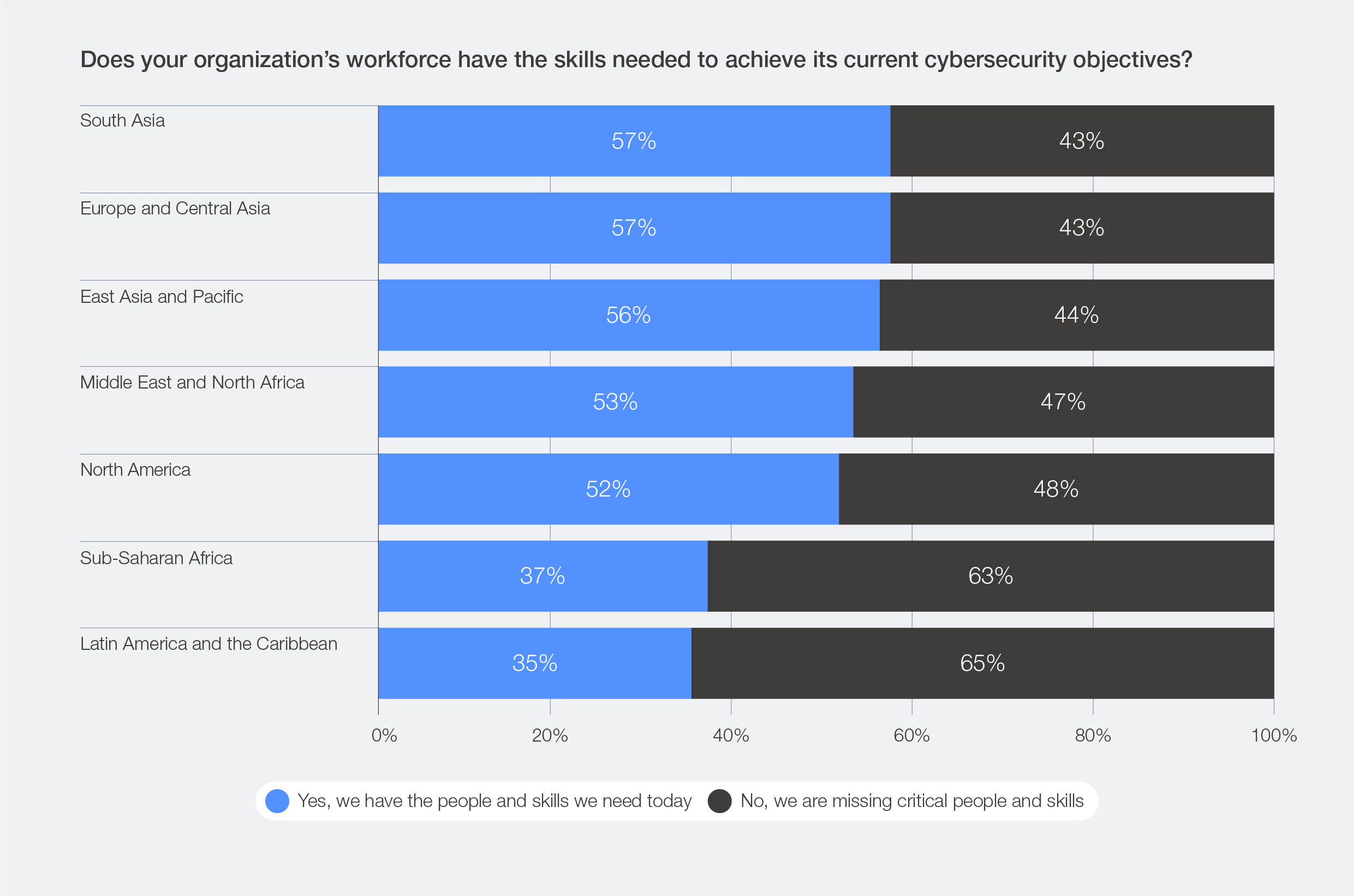
When viewed through a regional lens, cybersecurity talent shortages are most acute in Latin America and the Caribbean, where 65% of organizations reported lacking critical people and skills to meet cybersecurity objectives, and in sub-Saharan Africa (63%).
Figure 44: Regional perspectives on cyber skills shortages
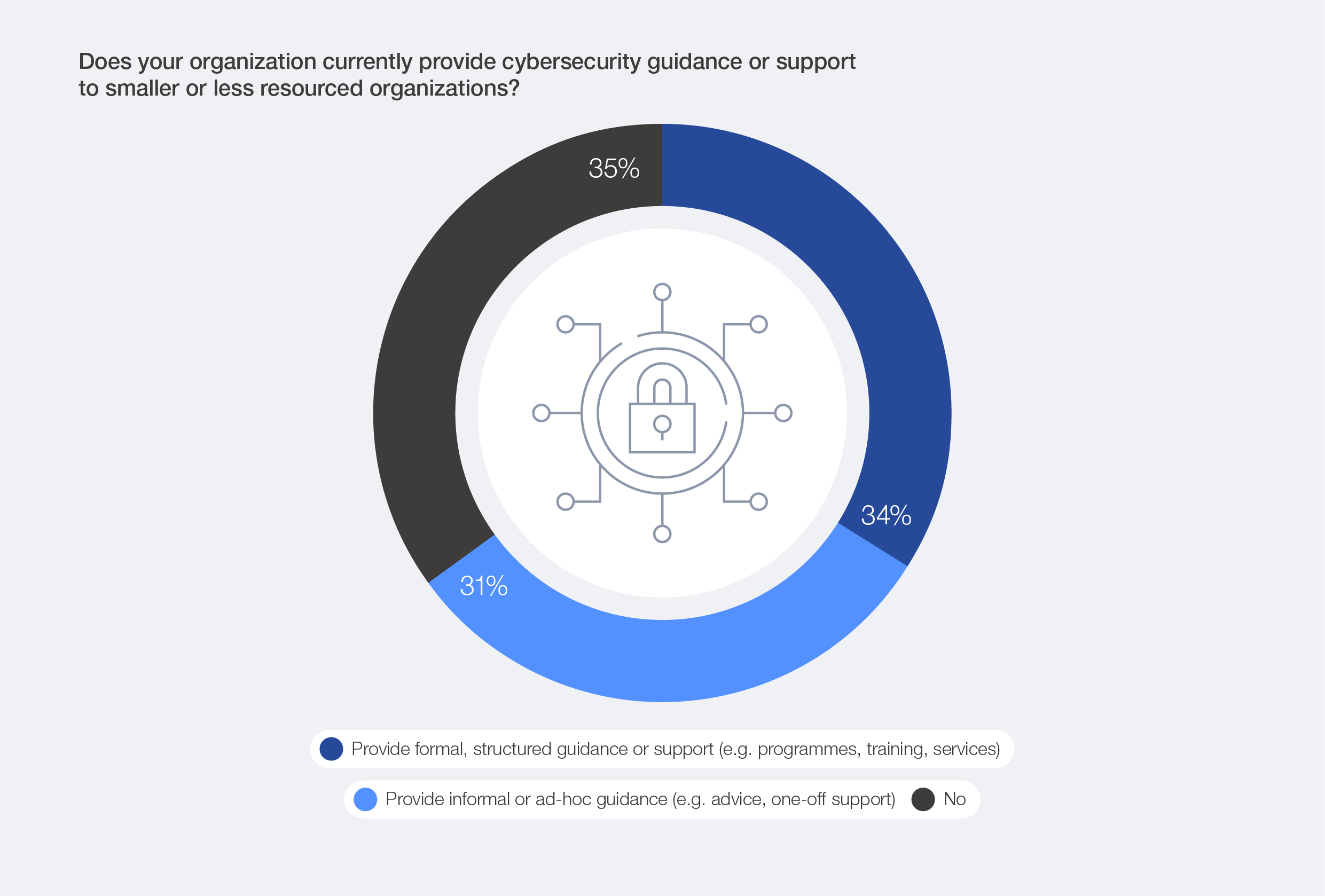
Encouragingly, some organizations acknowledge this imbalance and are taking steps to address it. Among experts surveyed during the Annual Meeting of the Global Future Councils and Cybersecurity 2025, 34% reported that their organizations provide formal, structured guidance or support – such as programmes, training or services – to smaller or less resourced partners. A further 31% said their organizations offer informal or ad hoc assistance.
Figure 45: How organizations support their ecosystem
Box 5: Addressing cyber inequity to ensure that cyber resilience is accessible to all
As cyber inequity deepens, the work of publicinterest cybersecurity actors has become essential to closing capability gaps for underserved organizations. The approach of CyberPeace Builders,48 for example, demonstrates how targeted, mission-driven support can shift resilience outcomes: by mobilizing skilled volunteers and providing tailored guidance, it helps NGOs strengthen their defences and maintain the continuity of their vital services. This model shows that when expertise is made accessible, organizations facing resource constraints can meaningfully improve their resilience.
However, no single initiative can meet global demand. Addressing cyber inequity at scale requires a sustainable ecosystem of cyber defenders – researchers, trainers, incident responders, tool builders and volunteer communities – working in coordination to maintain the infrastructure that underserved organizations rely on but cannot afford, and to provide tools and services where the market fails.
To support this ecosystem, broader efforts have emerged through Common Good Cyber49 to map what these organizations do, identify shared needs, strengthen capacity and enable deeper collaboration. A coordinated funding mechanism has also been launched to ensure that publicinterest cyber services can grow sustainably rather than depend on short-term, fragmented support.
By investing in and connecting these initiatives in the public interest, the global community can help address cyber inequity and ensure that cyber resilience is accessible to all, not just to those with resources.
Advances in AI are further deepening existing inequity
AI is emerging as both a transformative tool and a new source of inequity in cybersecurity. As AI capabilities become central to defence and detection strategies, unequal access to advanced technologies, data and expertise risks deepening the divide between well-resourced and resource-constrained organizations. At the same time, AI is often embedded into updates and released as new features, making it harder for organizations with limited resources to fully understand, govern or control its introduction.50
More than half of all respondents (54%) identified limited knowledge and skills as a key obstacle to adopting AI-driven solutions for cybersecurity.
Larger organizations (by revenue) are emerging as early leaders in leveraging AI-driven threat detection and automation. As the Global Cybersecurity Outlook survey data highlights, companies with higher balance sheets report higher AI adoption rates, while smaller entities (by revenue), governments and NGOs tend to lag behind. Beyond these findings, expert interviewees noted that some industries progress more rapidly due to greater technical maturity and investment capacity, while others remain constrained by financial, regulatory or procedural barriers – further reinforcing existing disparities in cybersecurity preparedness.
Figure 46: Use of AI-enabled cybersecurity tools, by company size and sector (revenue)
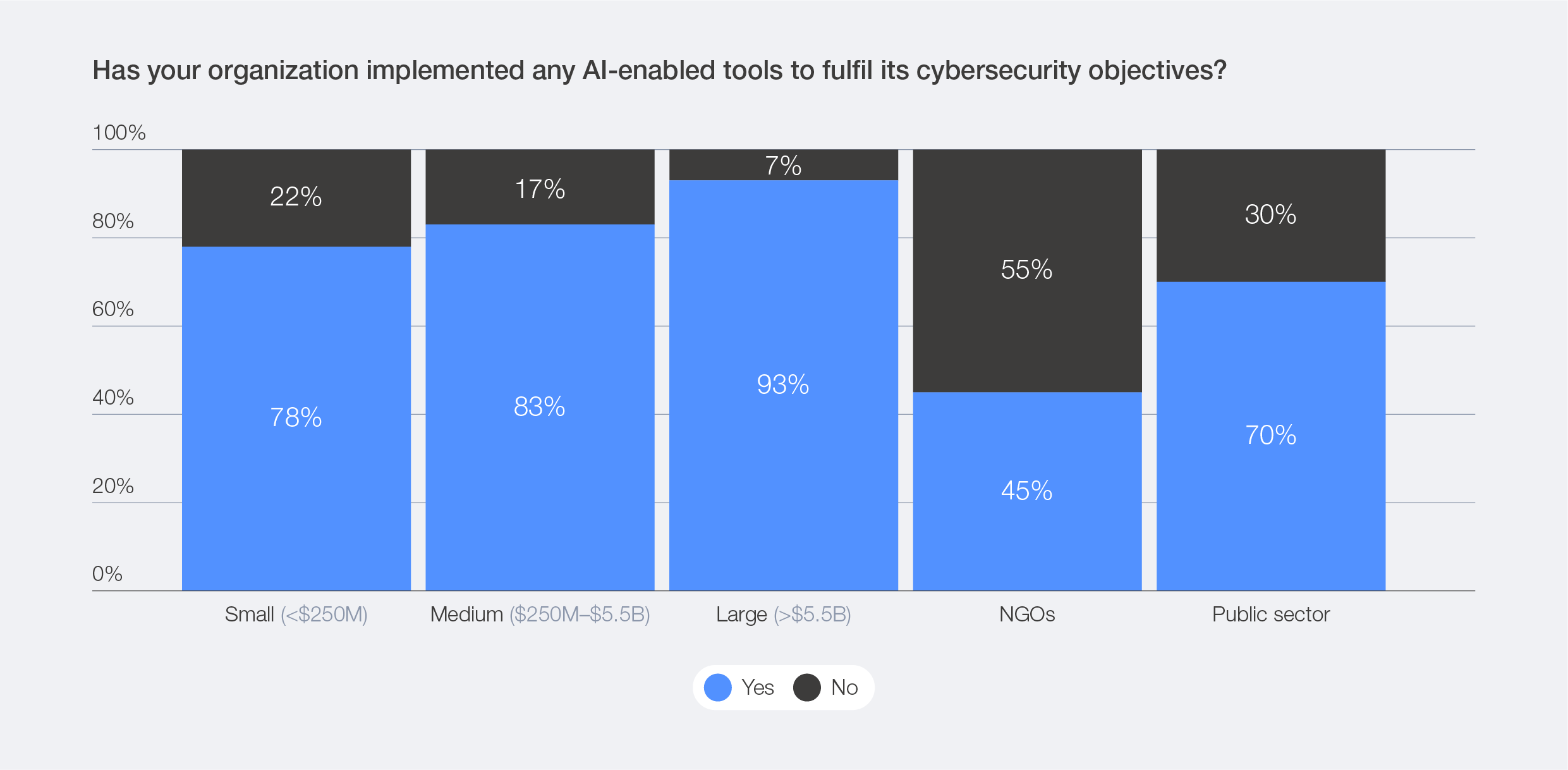
Within interconnected supply chains, these differences in capabilities significantly increase systemic exposure: adversaries can target less-protected partners to infiltrate high-value organizations downstream. A vulnerability in one supplier today may become another organization’s breach tomorrow. This shift underscores the growing importance of viewing security through an ecosystem lens, where the resilience of one actor depends on the vigilance of all.
Cyber inequity isn’t simply a matter of different budgets or geographies – it is the invisible fault-line where those lacking access to security skills, resources and awareness are perennially targeted by countless bad actors. The actual capability gap lies not just in technologies, but in people: in the professionals needing more training and support, and in the underfunded small- to medium-sized businesses and other similarly positioned entities that make up 90% of our global ecosystem, which cannot keep pace with evolving threats. Bridging this divide requires more than well-meaning intentions that habitually fail to garner holistic, top-down, organization-wide support. It demands vendor-neutral education/credentialling, mentorship and a receptive, global mindset powered by diverse, inclusive collaboration.
— Illena Armstrong, President, Cloud Security Alliance
3.7 Future threat vectors are emerging in silence
While AI continues to dominate the cybersecurity landscape, several other technologies and threat vectors are quietly gaining traction in the background and are expected to affect cybersecurity by 2030.
Drawing on a focus group session with members of the Global Future Councils – including Artificial General Intelligence, Clean Air, Cybersecurity, Data Frontiers, Decentralized Finance, Energy Technology Frontiers, Generative Biology, Geopolitics, Information Integrity, and Next-Generation Computing – it is possible to integrate their forward-looking perspectives with data from the Global Cybersecurity Outlook 2026 survey to reveal the emerging risks likely to define cybersecurity in the coming years.
Our digital world runs through cables lying deep beneath the ocean’s surface. With 99% of international data traffic flowing through them, these undersea systems are the unseen lifelines of our global economy – and they are also uniquely vulnerable. A single break can disrupt essential services and daily life for billions. Building true resilience means moving from awareness to action: faster repairs, more diverse routes, and international cooperation that matches the critical nature of these assets.
— Doreen Bogdan-Martin, Secretary-General, ITU
Autonomous systems and robotics
Some 26% of survey respondents indicated that autonomous systems and robotics will affect cybersecurity in 2026, and according to experts in the Global Future Councils, this proportion is expected to rise by 2030. By the end of the decade, autonomous systems will be a near-term factor, from AI assisting analysis to directing physical actions in factories, logistics, healthcare and public spaces. This evolution could create a new cyber‑physical risk profile, where machine‑executed decisions can alter safety and service quality within seconds, compressing detection and response windows. Interdependencies are likely to deepen as autonomous workflows lean on shared cloud platforms, models and data, meaning disruptions or errors could propagate rapidly across operations and supply chains. Physical AI is becoming a security concern, as intelligent robots – such as those now used for order-picking in warehouses or moving containers in ports – evolve from simple machines to adaptive systems, making their behaviour less predictable and more vulnerable to compromised learning processes or control software. Securing these systems requires embedded cybersecurity by design, strong access controls for human–robot interaction and continuous monitoring to maintain operational integrity.
Digital currencies
By 2030, digital currencies are expected to play a growing role in daily economic activity, with broader adoption across retail payments, payroll systems and selected public and cross-border services.51 This ubiquity makes them both foundational and fragile. Cyberattacks targeting exchanges, wallets and smart-contract infrastructure have already caused multibillion-dollar losses, and by 2030 such incidents could have systemic consequences, triggering potential liquidity shocks or eroding confidence in national and corporate digital assets.52 In 2025, for instance, a major crypto-exchange breach attributed to a state-linked threat group resulted in losses exceeding $1.5 billion, with investigators estimating that nearly a fifth of the stolen funds were rapidly converted into unrecoverable assets – a stark reminder of how quickly digital liquidity can vanish in emerging regulatory contexts.53 As synthetic identities and AI-driven fraud evolve, real-time verification and resilience of settlement networks will define trust in the financial system. Interdependencies among decentralized finance, central-bank digital currencies and autonomous payment agents mean that disruption in one layer can quickly ripple through others. In this environment, digital currencies have become critical infrastructure whose security underpins economic and societal stability.
Space technologies and undersea cables
Space and seabed infrastructure remain comparatively overlooked in cyber risk planning, despite enabling core functions of critical infrastructure. In 2026, 9% of respondents indicated that space technologies will most significantly impact cybersecurity. Looking ahead to 2030, satellite-based positioning, navigation and timing will be even more essential for aviation, maritime activities, power-grid coordination and financial transactions. At the same time, satellite communications and undersea cables will form the backbone for emergency services, cloud infrastructure and international data exchange.54 Despite this, only 15% of respondents consider space assets, and 18% account for undersea cables, in cyber risk mitigation. With the growth of AI-driven operations, cloud services and autonomous systems, organizations will increasingly rely on precise timing, navigation and robust data connections. This heightened dependence means that even small disruptions in satellite or undersea cable infrastructure could trigger widespread impacts across entire digital ecosystems.
Natural disasters and climate change
By 2030, the convergence of climate volatility and digital dependency will have transformed natural disasters into complex cyber-physical crises. Extreme weather, prolonged droughts and heatwaves routinely disrupt power, data and logistics networks, while AI-driven coordination systems for energy grids, water and emergency response introduce new attack surfaces. As renewable energy and storage infrastructures expand, their dense networks of inverters, sensors and cloud-linked controllers multiply points of cyber exposure. Climate-related shocks increasingly coincide with misinformation and organized influence operations that capitalize on confusion during emergencies, eroding confidence in institutions. Cross-border impacts – such as satellite degradation from solar storms or undersea cable damage from seabed shifts – underscore how physical events cascade through digital infrastructure. By 2030, climate may not just be a background stressor but a persistent amplifier of cyber risk, extending recovery times and blurring the line between environmental and digital resilience as emerging technologies combine and create cumulative risks that can compound the effect of climate-driven disruptions.
Quantum technologies
In 2026, 37% of Global Cybersecurity Outlook survey respondents believe quantum technologies will affect cybersecurity within the next 12 months. This reflects expectations of greater investment, stronger regulatory momentum and a faster pace of digital transformation in the year ahead. By 2030, quantum will have evolved from a theoretical disruptor into a selective but material threat to cryptography. State-level or well-resourced actors may be capable of quantum-accelerated attacks on high-value targets, even as full-scale code breaking remains rare. At the same time, defenders will harness quantum-enhanced analytics and sensing for anomaly detection, creating a dynamic attacker– defender race. The greatest systemic exposure will come from legacy encryption in embedded and industrial systems that cannot easily migrate. Driven by increased timelines and awareness – including the availability of National Institute of Standards and Technology (NIST) standards and guidance introduced in 2024, as well as tight migration deadlines set by national cybersecurity agencies – regulations are taking more decisive action and providing clearer guidelines for the transition to post-quantum cryptography.55 The window for proactive migration to these new cryptographic standards is closing fast. Those who delay will find that quantum readiness has become the next frontier of systemic cyber risk.